View analytics for the group level only
At the group level, you can see graphs, tables, and metrics that only are in its Analytics section, meaning that these metrics are not found in any other section. The following are the group analytics.
Group availability
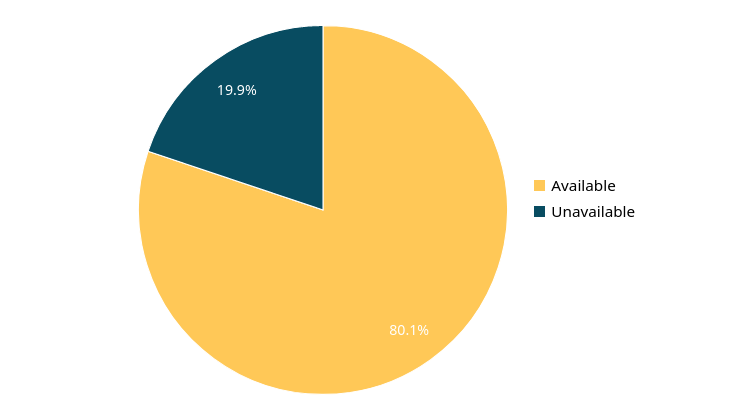
The percentage of time that the group has unsolved Events compared to the entire existence of the group.
Days since group is failing
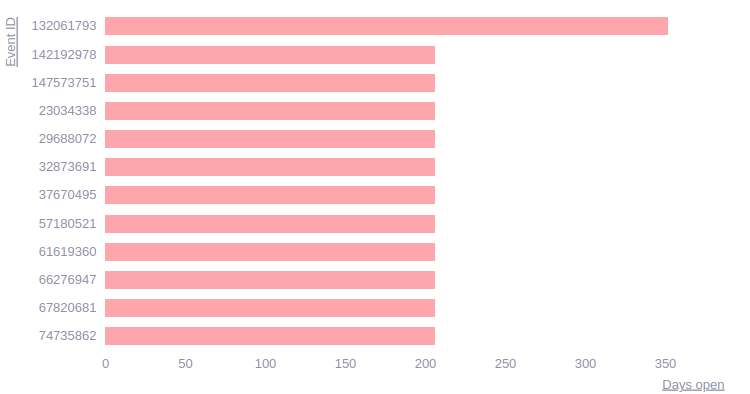
Here you can see the number of days since each Event is unsolved.
Findings by tags
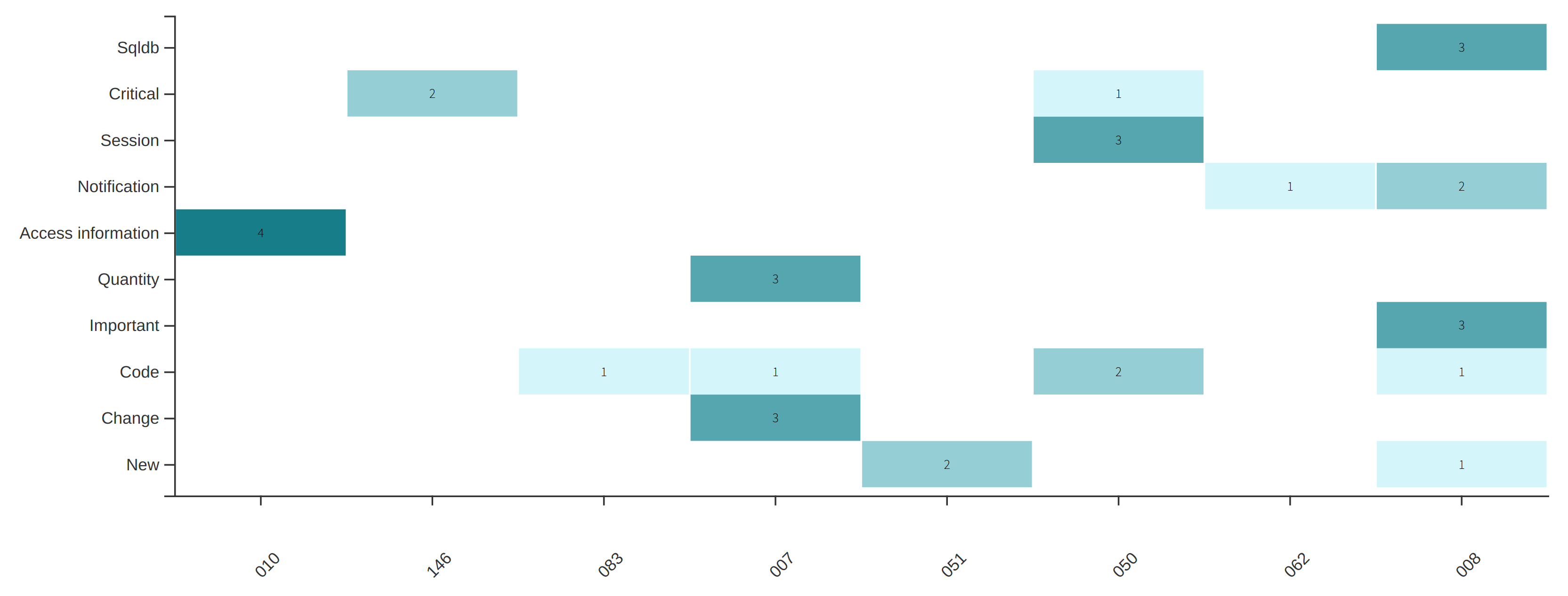
These are all your findings categorized by tag. Tags can be assigned at the moment of defining a treatment for your vulnerabilities, for more information click here.
CI Agent-related analytics
By enabling DevSecOps you get access to a Docker container built specifically to verify the status of security vulnerabilities on your system. You can embed this container into your continuous integration system to look for changes in security vulnerabilities:
-
DevSecOps is fast and automatic, as it is created by the same intelligence of the hackers who already know your system in-depth.
-
In case the DevSecOps agent finds one vulnerability to be open, we can (optionally) mark the build as failed. This strict mode can be customized with severity thresholds and grace periods according to your needs.
-
Statistics from over a hundred different systems show that DevSecOps increases the remediation ratio and speed, helping you build a safer system and be more cost-effective throughout your software security development life cycle (SDLC).
Service status

Here you can see if the CI Agent is active or inactive.
Service usage

Number of times your team used the CI Agent to check for vulnerabilities.
Repositories and branches

You can run the CI Agent in any of your repositories at any of its versions (commits or branches).
Your commitment towards security
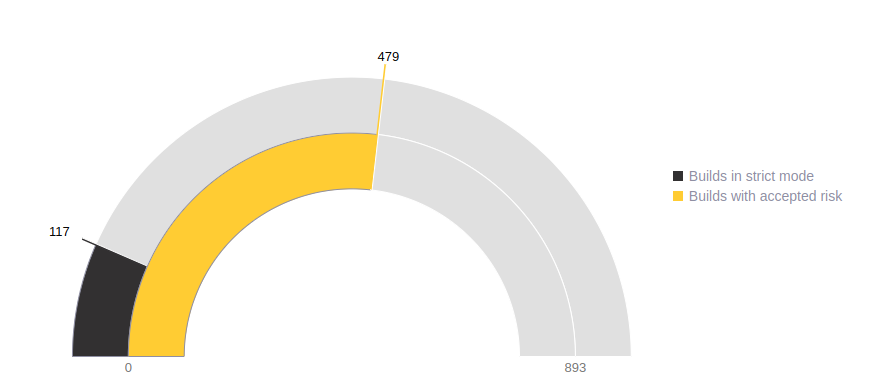
The CI Agent's objective is to help your team overcome security vulnerabilities. For this to work, we put two things in your hands:
- The strict mode (which is enabled by default) helps you stop builds or deployments if there are open vulnerabilities, and thus protects your system from vulnerable code introduction.
- However, accepted vulnerabilities on Fluid Attacks' platform are ignored by the strict mode, and the agent will (by decision of your team) allow them to be built or deployed.
The maximum benefit is reached when the accepted risk is low, and the strict mode high.
Builds risk
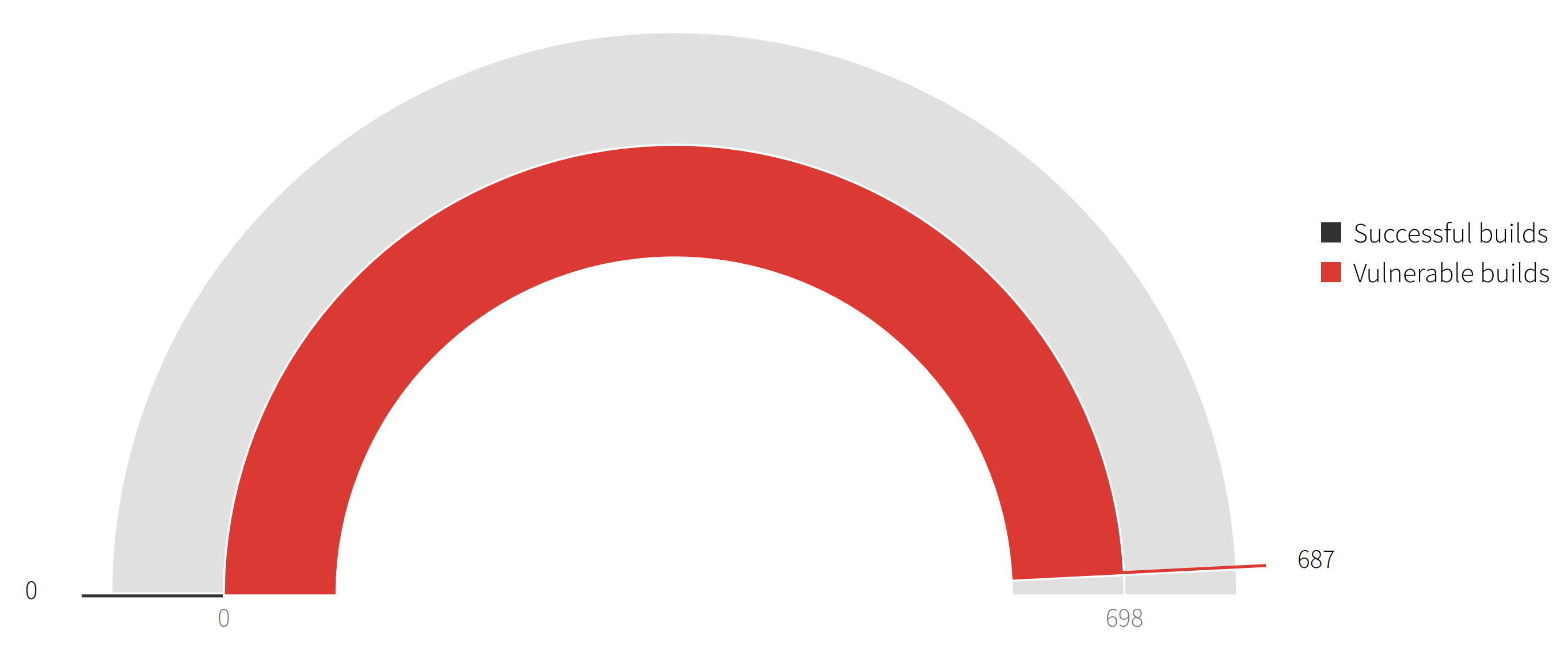
Risk is proportional to the number of vulnerable changes introduced into your system:
- A build is considered vulnerable if it contains security issues.
- The CI Agent in strict mode stops those security issues from being delivered to your end users.
