Manage your credentials
View organization credentials table

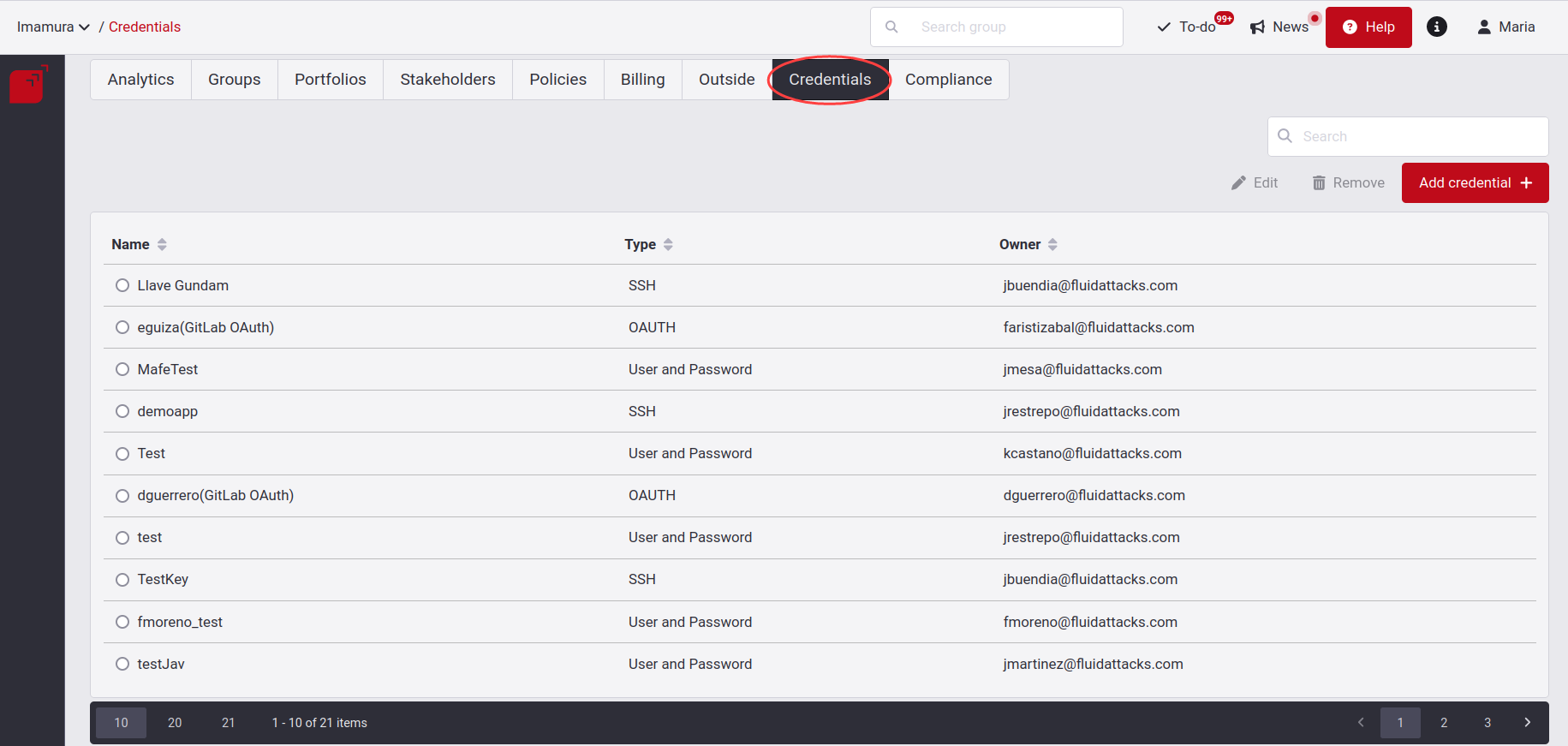
- Name: The name of the credential.
- Type: Which type of credential it is, can be HTTPS, SSH, Azure DevOps PAT or Cross-account AWS IAM role. You can also see in this column the connection of the providers via OAuth.
- Owner: The person who created the credential.
Add credentials

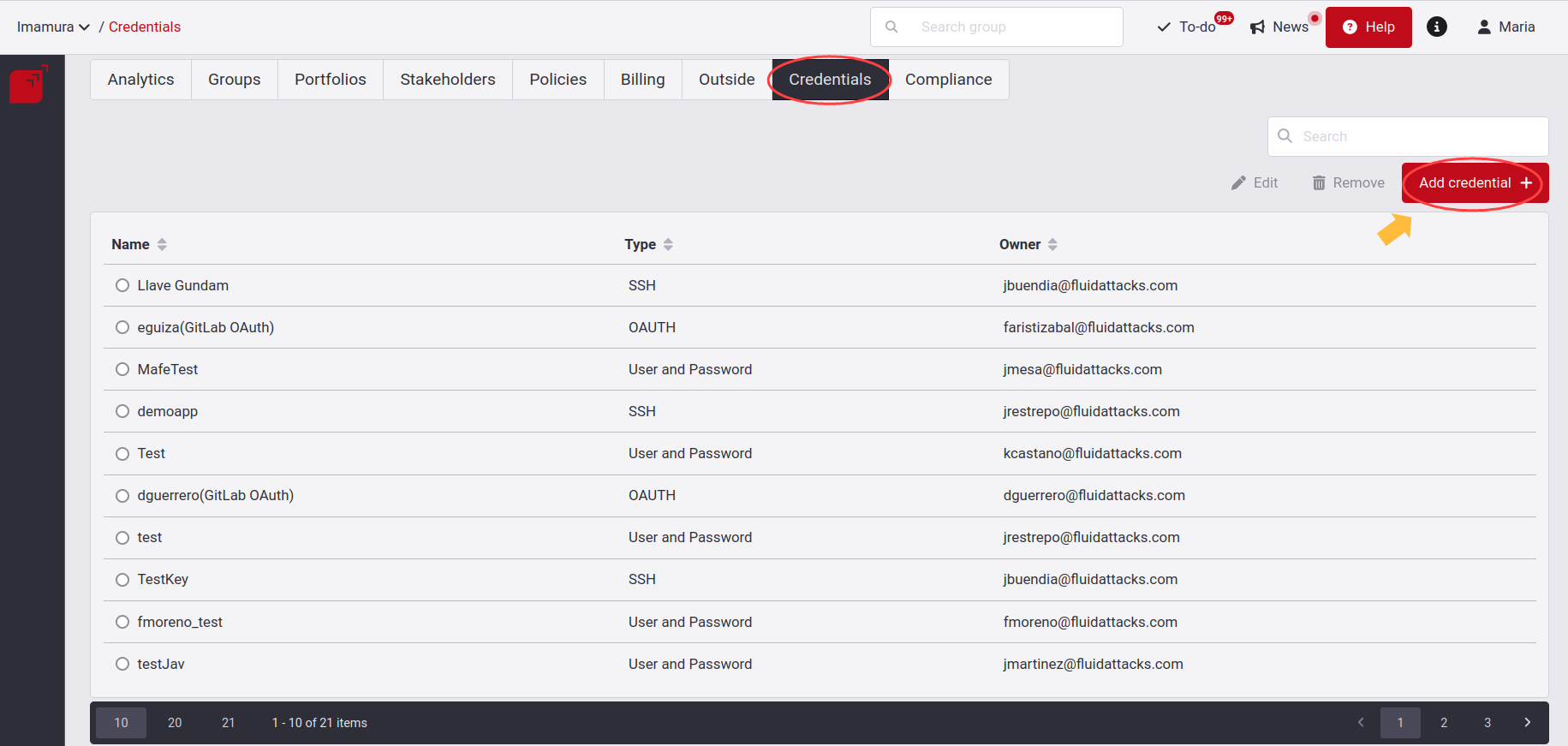
Clicking on it will allow you to add via OAuth or individually.
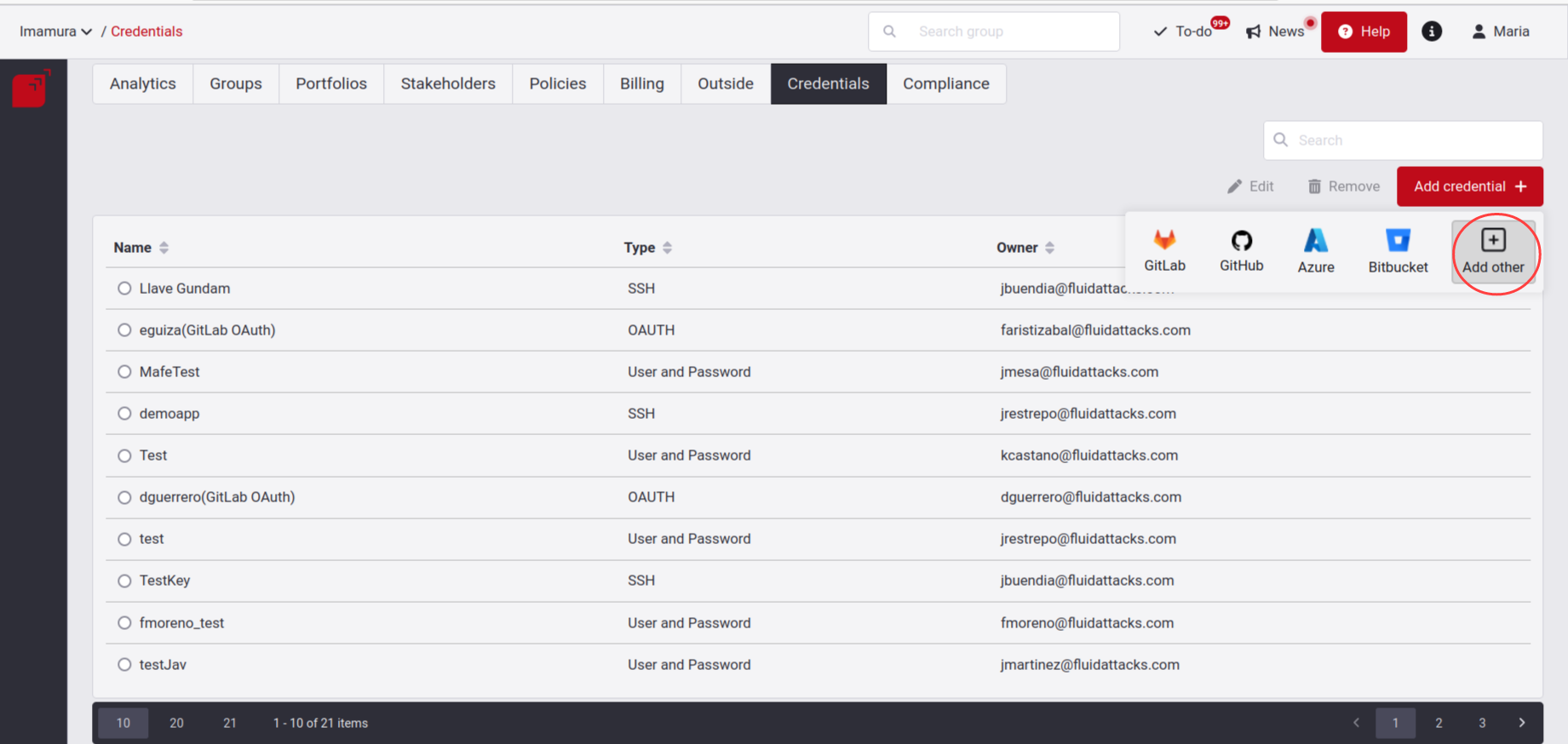
Below we show you how to add it individually; if you want to know how to do it via OAuth, you can enter here.
When you click on Add other, you will get a pop-up window where you can add new credentials.
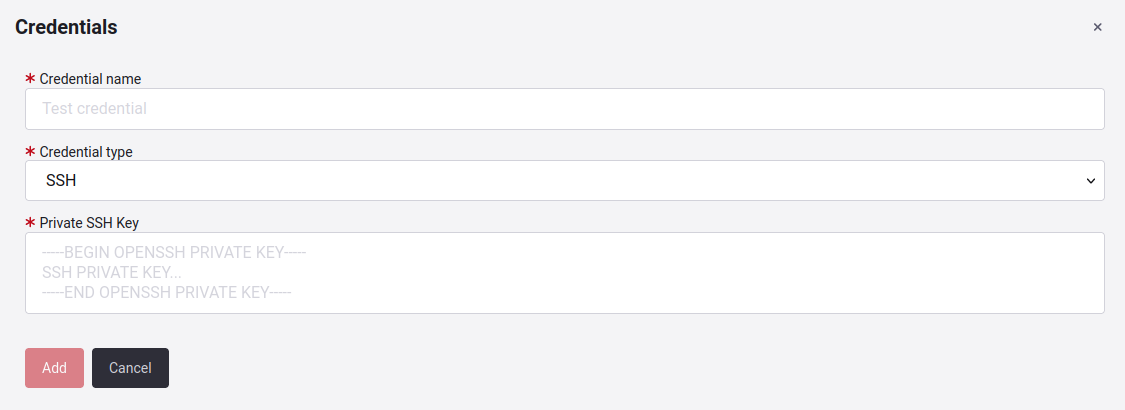
Here, you will have to enter a unique credential name and select the credential type ( HTTPS, SSH, Azure DevOps PAT or Cross-account AWS IAM role).
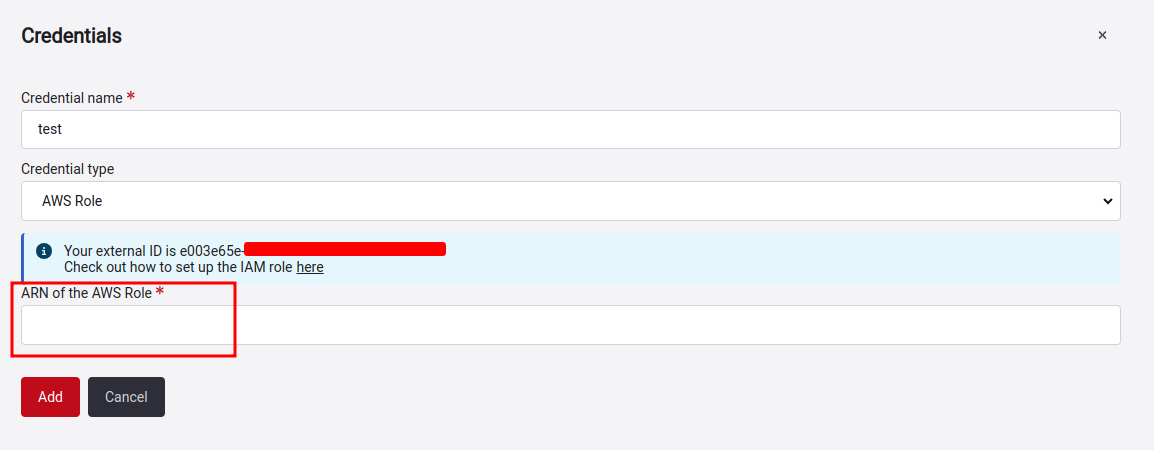
For this, we will provide you with an external ID. This ID is unique and we will use it as a private key that allows us to assume the role you will create in a more secure way; that's why you must use it as is in the creation of the role. Click here for more information on how to create the role.
Note: Keep in mind that if your organization has more than one AWS account, you can create the role on as many of them as you need and provide the correct ARN when prompted while adding the respective credentials.
Edit credentials

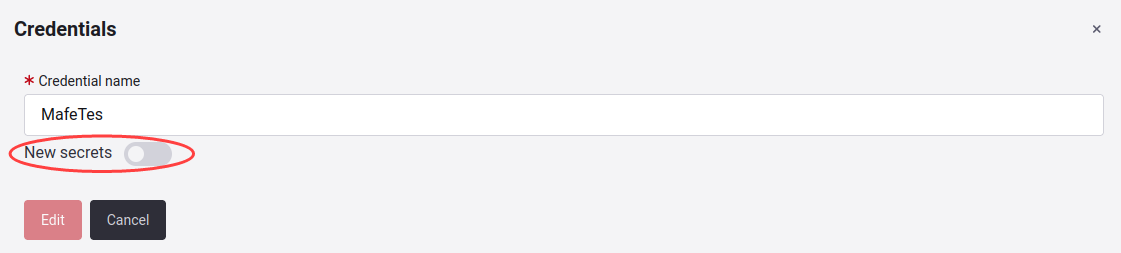
According to the Credential type will enable the fields for editing.
Remove credentials

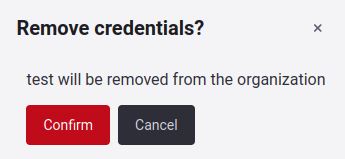
The following are some points to keep in mind regarding credentials:
- If the credential is removed, it is also removed from all the git roots used.
- When a member is removed from the organization, then their credentials are removed from that organization.
- The owner of the credentials is the last one that edited the credential's secrets.
Search the credentials table
