Manage general policies
Manage your organization's general policies
 Role required: User Manager
Role required: User Manager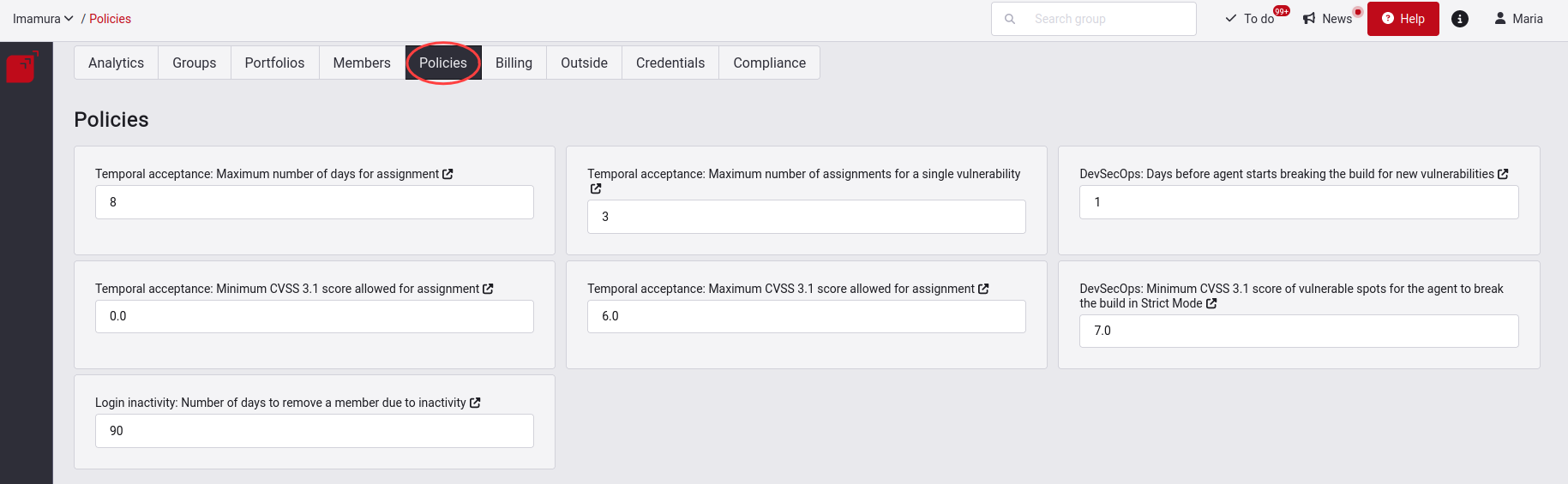
In this section, you will find three tables. The first one allows you to define values for eight general policies within your organization. The first four policies specify the conditions for the temporary acceptance of vulnerabilities; the next two, for breaking the build; and the last one, for defining an inactivity period for the platform usage. Below we explain each of the seven policies you can set up.

Maximum number of calendar days a finding can be temporarily accepted
Here you define the maximum number of calendar days that a finding can be temporarily accepted; this limit can be at most 31 calendar days. This policy affects the execution of the DevSecOps agent in case you are using it, since temporarily accepted vulnerabilities will not be considered at the time of breaking your build. This means that you have to be careful when setting this number to prevent some vulnerabilities remaining unresolved for a long time, which increases the risk to your applications.
Maximum number of times a finding can be accepted
Here you define the maximum number of times that a vulnerability can be temporarily accepted. If, for example, you set this number as one and accept a vulnerability temporarily, after the acceptance period passes, or you change the treatment of that vulnerability or remediate it, you won't be able to accept that same vulnerability again in the future. This number can be any number you deem appropriate.
Grace period where newly reported vulnerabilities will not break the build
Period in days (DevSecOps only). Here you define the period in days that you allow a vulnerability to be open without it causing the DevSecOps agent to break the build.
Minimum CVSS v3.1 score of an open vulnerability to break the build
Score to break the build in strict mode. Here you define the minimum value of the CVSS v3.1 score (values from 0.0 to 10.0) that a vulnerability has to have in order for the DevSecOps agent to break the build.
Minimum CVSS v3.1 score allowed for temporary acceptance
Here you define the minimum range in severity score, according to CVSS v3.1, within which you want vulnerabilities to be temporarily accepted.
Maximum CVSS v3.1 score allowed for temporary acceptance
Here you define the maximum range in severity score, according to CVSS v3.1, within which you want vulnerabilities to be temporarily accepted. This means that you can control the maximum risk you are willing to take.
Number of days until vulnerabilities are considered technical debt and do not break the build
Grace period before a vulnerability is considered "technical debt" and does not break the build. Here, you define the number of days vulnerabilities break the build once reported. After this period, vulnerabilities will be considered technical debt and will not break the build.
Number of days after which a member is removed due to inactivity
Here you define the number of days of allowed inactivity before a member is removed if they do not login to the platform. The given member is removed completely and all the granted access to organizations and groups will be revoked. In case the user wants to access those resources again, once the removal due to inactivity has been performed, they have to request a new invitation to the organization or group User Manager.
Manage your general policies at a group level
 Role required: User Manager
Role required: User Manager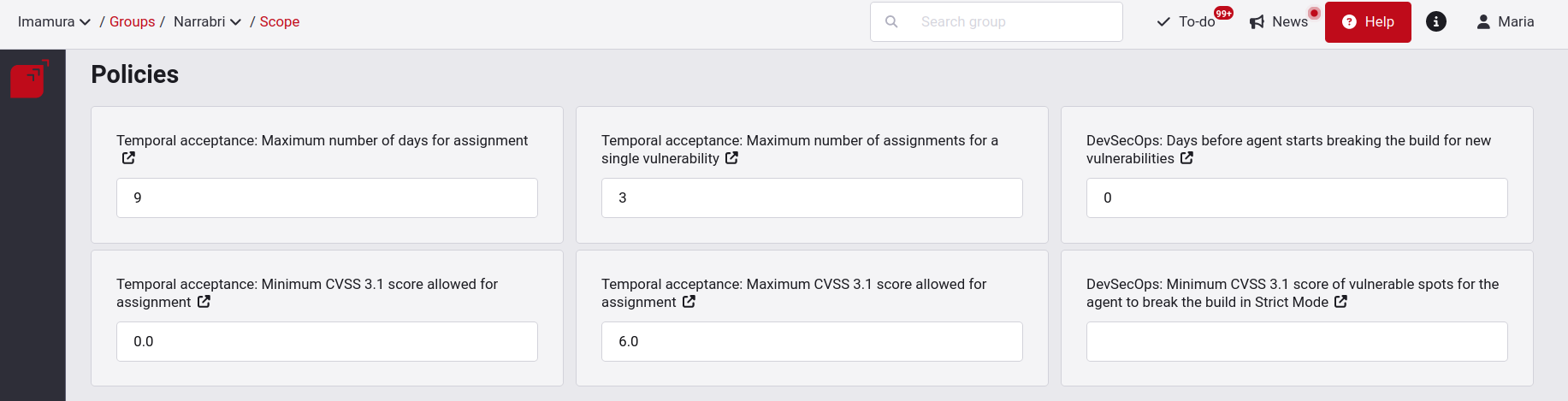
To change the default values (which are inherited from the policies at the organization level), go to the field you want to modify and click on the Save button.

You will get a notification announcing the policy change.