Download a report of detected vulnerabilities
Download a group's vulnerability report

The available report options have either summarized and easy-to-read information or complete and technical information about the vulnerabilities that have been reported in a specific group. In the Reports window, you can see the following options:
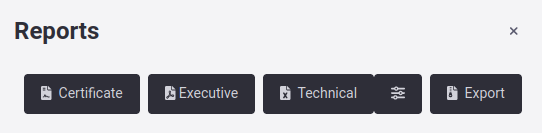
Certificate: This option generates a security testing certification. You must have filled out the information section for this certificate to be generated.
Executive: This option creates a summarized report in PDF of all vulnerabilities reported in the group, tailored to a management perspective.
Technical: This option generates a much more in-depth report in XLSX of all vulnerabilities reported in the group, or filtered by Treatment, suitable for those who want all the technical details. Note that you can apply filters when generating this report. For more information, click here.
Export: This option creates a ZIP file with an export of all vulnerabilities reported in the group (includes the previous reports and files of compromised records and evidence).
Note: The Certificate option is only available to members with the User Manager role.
Once you have registered your number, in order to obtain the requested report, you must enter another verification code that will be sent to your mobile, as you can see below:
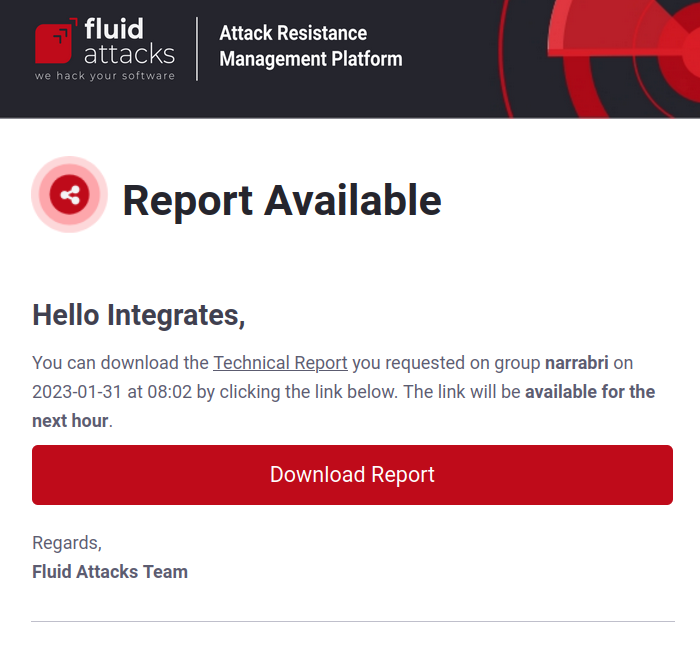
As immediately announced by a message in Fluid Attacks' platform, it will send you an email with a link to the report in a couple of minutes. Once you receive it, clicking on the Download Report button will allow you to download the report to your device. It is essential to note that the access granted through the link is only available for one hour.
Note: Please note that there may be restrictions on sending the OTP code by SMS in Canada.
Definitions of the Technical report columns
- Related Finding: Vulnerability type
- Finding Id: Vulnerability identifier composed by random numbers and letters
- Vulnerability Id: Location identifier composed by random numbers and letters
- Package: Name of package that is vulnerable
- Vulnerable version: The version of the package
- CVE: CVE identifier
- Where: Location of the vulnerability found with the specific path where it is located
- Stream: Steps to reach the vulnerability in dynamic environments
- Specific: Indicates exactly where the vulnerability was found (line, field or port)
- Description: Vulnerability description.
- Status: Vulnerability status, which can be Safe or Vulnerable
- Severity: Vulnerability score based on CVSS v3.1 standard
- Requirements: Unfulfilled Requirement(s) based on security standards
- Impact: How your application is affected by the related vulnerability
- Threat: How the attacker can exploit the system
- Recommendation: Suggestions that can be applied to fix related vulnerability
- External BTS: Customer Bug Tracking System URL used to fix the vulnerability
- Compromised Attributes: Data or information that was compromised as a result of exploiting the vulnerability (e.g., users, IDs, passwords)
- Tags: Tag to identify the vulnerability
- Business Critically: Numerical value to classify the severity of vulnerabilities defined by customers for their internal use
- Technique: Security testing technique used to identify the specific vulnerability
- Report Moment: Vulnerability confirmation date
- Close Moment: Vulnerability fixing date
- Age in days: Days have passed since the vulnerability was confirmed
- First Treatment: First confirmed treatment defined to the vulnerability
- First Treatment Moment: Date on which the treatment was defined
- First Treatment Justification: Treatment applied justification
- First Treatment expiration Moment: For Temporal treatments, this date shows the date which treatment expires
- First Assigned: Who was the first person to be assigned this vulnerability
- Current Treatment: The current treatment of the vulnerability
- Current Treatment Moment: Date on which current treatment was applied
- Current Treatment Justification: Justification for applying current treatment
- Current Treatment expiration Moment: Expiration date for current treatment
- Current Assigned: The name of the person who is currently assigned to the vulnerability
- Pending Reattack: Whether they have requested a reattack or not
- # Requested Reattacks: The total number of times reattacks have been requested
- Remediation Effectiveness: The effectiveness percentage of the remediation of that vulnerability
- Last requested reattack: The date on which the most recent reattachment was requested
- Last reattack Requester: Email of the user who requested the most recent reattack
- CVSSv3.1 string vector, Attack Vector, Attack Complexity, Privileges Required, User Interaction, Severity Scope, Confidentiality Impact, Integrity Impact, Availability Impact, Exploitability, Remediation Level and Report Confidence: All these columns are part of the Severity Score CVSS values
- Commit Hash: Commit identifier where the vulnerability was found
- Root Nickname: The nickname of that root where the vulnerability was found
Filter the Technical report

When you click on it, a pop-up window will appear where you will be able to select what information you want to generate, finding four different filter options:
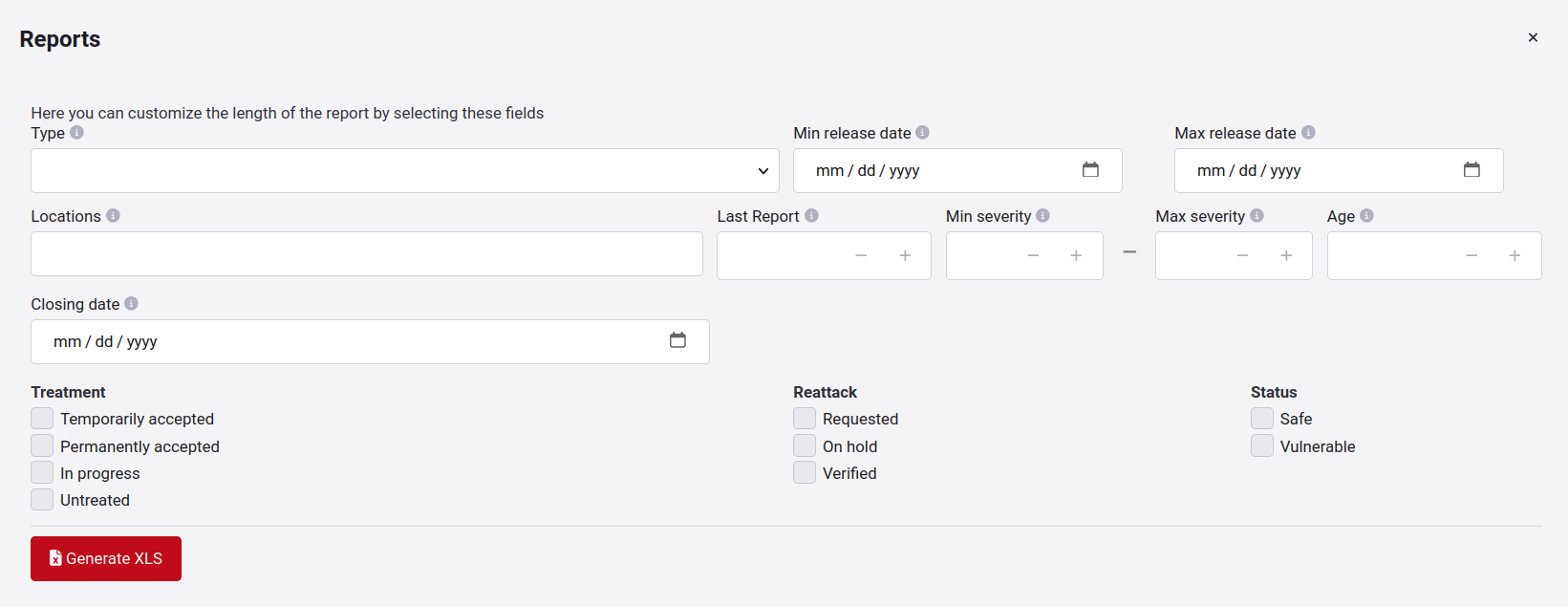
- Type: Filter by the name of vulnerability type
- Min release date: Filter the vulnerabilities with the most recent date when the vulnerability was reported
- Max release date: Filter vulnerabilities with the oldest date it was reported
- Locations: The localization of vulnerability
- Last Report: Filter types by days since the last reported vulnerability
- Min - Max severity: Filter out vulnerabilities with min and max severity value
- Age: Filter the vulnerability according to the age it has
- Closing date: Filters closed locations with a date equal to or before the specified date
- Treatment: Filter locations according to treatment
- Reattack: Filter locations according to their Reattack status
- Status: Filter vulnerabilities according to Vulnerable/Safe state
When you apply the filters of your interest, click on the Generate XLS button. You will receive the verification code on your cell phone; after successful verification, you will receive the report in your email with the selected data.
Download a report of all vulnerabilities in the organization

To download your organization's vulnerabilities (including all vulnerability statuses) in a .CSV file, go to the Analytics section at the organization level and click the Vulnerabilities button.
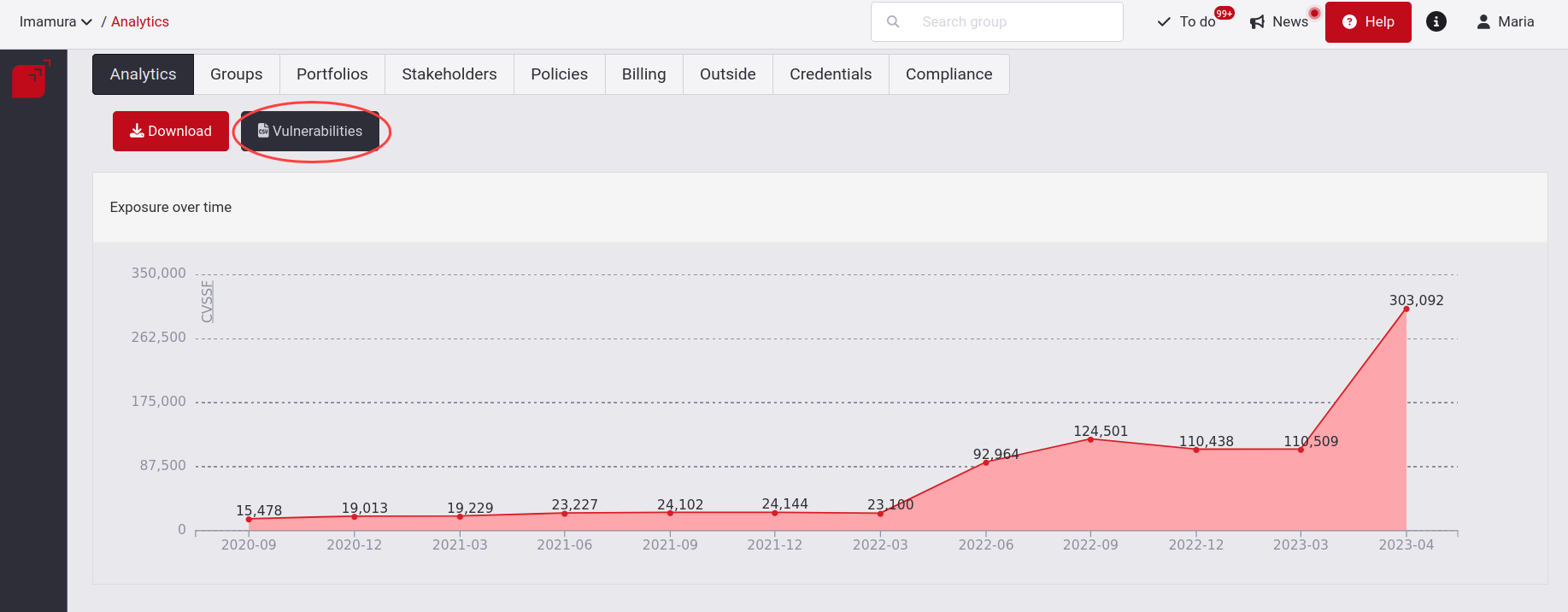
When you click on it, you will be asked for a verification code that will be sent to you via SMS, call or WhatsApp message. If you have not yet registered your phone number to Fluid Attacks' platform or need to update it, we invite you to read the information here.
When you enter the verification code, you will download a compressed file where you will find the file with a .CSV extension. When you open it, you will be able to see all the vulnerabilities of the organization. You can also get this information via API with the vulnerabilitiesUrl method. To know how to make the API request to our platform, we invite you to click here.