Architecture
Here you will find the high-level architecture
for the Connector connection
used by Fluid Attacks
as well as its minimum requirements
and limitations.
This solution relies on Cloudflare Connector.
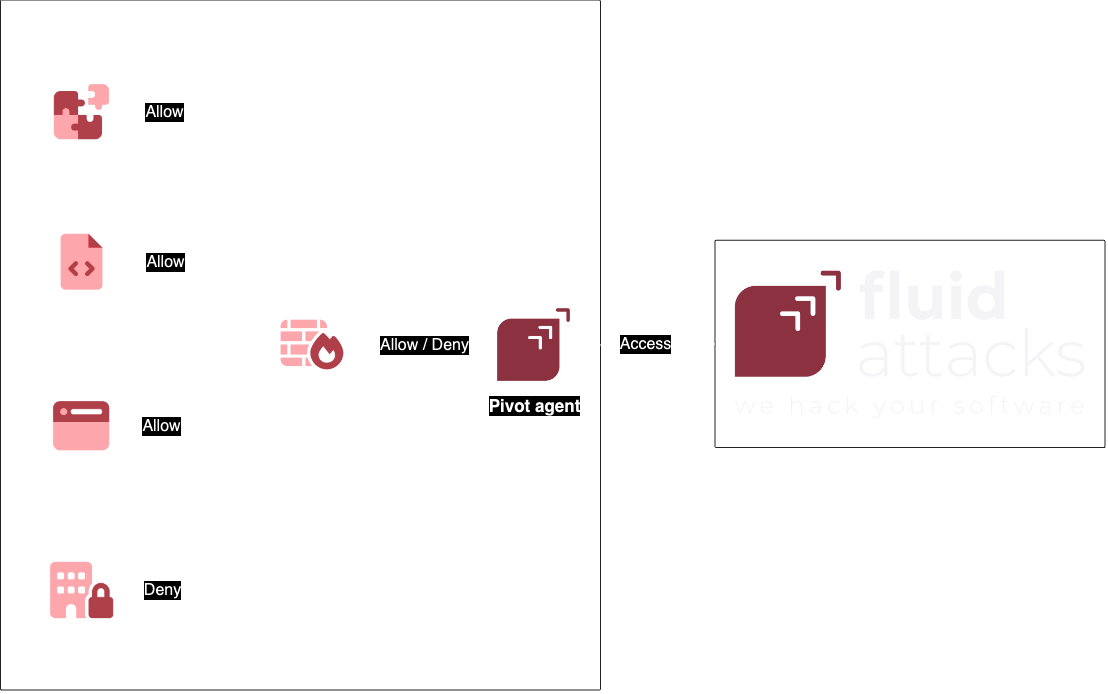
High-level architecture
We use a pivot agent
in order to access your resources.
The pivot agent is installed in
a container or server within your private network
and will be the one accessing
the private resources you expose to it.
Below is a high-level diagram that shows how the connection works.

Pivot agent minimum requirements
- 1 CPU
- 2 GiB of memory
- At least 5GB of free disk space
- A user with administrative privileges
- Docker, Linux, Windows or macOS
- Stable access to the Internet
- Firewall permissions for pulling the cloudflared Docker container or downloading the cloudflared agent
- Firewall permissions for reaching Fluid Attacks' Cloudflare network
- Firewall permissions for reaching the internal resources Fluid Attacks' will be accessing
Limiting access for the pivot agent
Fluid Attacks uses the pivot agent
for accessing your private network.
We recommend creating minimum privilege firewall rules for it in order to only expose those resources that are necessary.
Service limitations
Restricted IP addresses
There are several IP addresses
that are reserved by our system
and thus cannot be routed through a Connector connection.
- Routing within Fluid Attacks' internal network:
192.168.0.1
- DNS resolution within Fluid Attacks' internal network:
192.168.0.2
- Reserved for internal testing:
192.168.0.60192.168.1.60192.168.10.60192.168.100.60192.168.100.61192.168.100.62192.168.100.63192.168.100.64
Please make sure you do not expose such IP addresses
to the pivot agent
as this may cause service disruptions.
Maximum hosts
In order properly record network and HTTP logs,
No more than 1024 hosts can be routed through a Connector connection.
Using self-signed certificates
When using self-signed SSL certificates within your private network, HTTPS traffic going through it will not be inspected, reducing the log detail that can be collected.
This is caused by the fact that the Cloudflare network does not trust certificates signed by non-trusted certificate authorities.
We recommend using SSL certificates signed by a valid certificate authority so navigation logs within the tunnel are fully detailed.
Additional support
If you require additional support, do not hesitate to contact us.