Skims
Skims is a CLI application that can be configured to analyze source code, web services, and other attack surfaces, and produces detailed reports with the security vulnerabilities found.
End Users are allowed to run Skims as a Free and Open Source vulnerability detection tool.
Integrates configures and runs Skims periodically to find vulnerabilities over the surface of Fluid Attacks customers as part of the Essential plan.
Externally the Scanner can be an alias of:
- Skims, when run by End Users.
- The combination of efforts between Skims and Integrates, when part of the Essential plan.
Skims refers only to the CLI application.
Public Oath
- Skims can be used by End Users as a Free and Open Source vulnerability detection tool.
- The Skims CLI can be found on DockerHub
- It has a low rate of False Positives, meaning that it only reports vulnerabilities that have an impact.
- When the existence of a vulnerability cannot be deterministically decided, Skims will favor a False Negative over a False Positive. In other words, it will prefer failing to report a vulnerability that may have a real impact over reporting a vulnerability that may have no impact.
Architecture
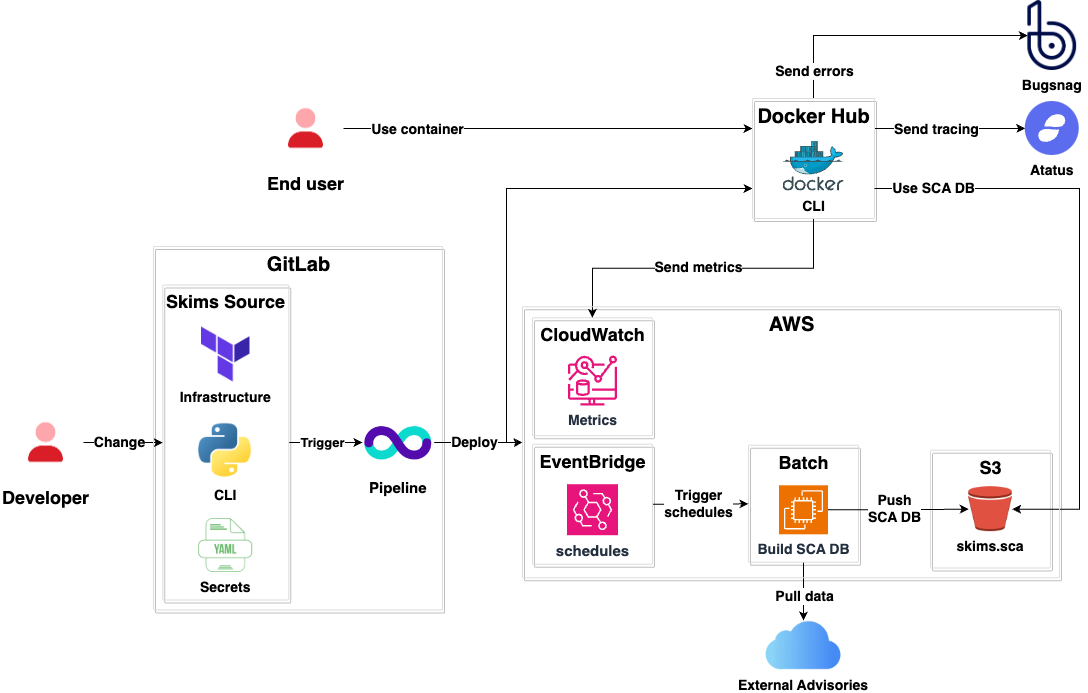
- Skims is a CLI application written in Python.
- It declares its own infrastructure using Terraform.
- Sensitive secrets like Cloudflare authentication tokens are stored in encrypted YAML files using Mozilla SOPS.
- Skims CLI is published on DockerHub so anyone can use it.
- The vulnerability advisories used for Source Composition Analysis (SCA) are managed by a schedule in the Compute component of Common. The schedule fetches the information from public vulnerability databases, and updates the data with new information. Once the data is ready, it is pushed to a public S3 bucket.
- Skims CLI performs SCA analysis with its own SCA DB.
- It sends tracing data to Atatus.
- It sends metrics data to AWS CloudWatch.
- It sends errors to Bugsnag
Contributing
Please read the contributing page first.
Development Environment
Follow the steps in the Development Environment section of our documentation.
When prompted for an AWS role, choose dev,
and when prompted for a Development Environment, pick skims.
Local Environment
Run this command within the universe repository:
m . /skims
This will build and run the Skims CLI application, including the changes you've made to the source code.
Local Tests
There are several skims tests, for each library or finding that has been added to the module.
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.