Main
-
BM01: Our target audience is anyone interested in cybersecurity. Therefore, we must use non-technical English as much as possible.
-
BM02: We must write blog posts that have some relation to cybersecurity. (We have a list of recommended topics here, but we can address many others; see the latest posts).
-
BM03: We must generate blog posts in the markup language Markdown. (Please refer to this document for Markdown rules.)
Title and subtitle
-
BT01: We should grab the readers' attention with the blog posts' titles, making them funny, thought-provoking or exciting. We can, for example, write a title as a question (e.g., "What's the Perfect Crime?") or address it directly to the reader (e.g., "I Saw Your Data on the Dark Web"), but we must not create a generic title (e.g., "SQL Injection").
-
BT02: We must write titles that do not exceed 35 characters.
-
BT03: In each case, we should create a subtitle that reflects the purpose or central idea of the blog post (e.g., "Get a digest of Internet crime over the last year," "Confusion with the cloud shared responsibility model").
-
BT04: We must write subtitles that do not exceed 55 characters.
Length and structure
-
BS01: We must write blog posts of between 800 and 1,200 words.
-
BS02: We should write blog posts with structures similar to the following (based on recommendations by the American Lecturer Robert Pozen):
- An introduction that contextualizes the reader, states the main theme, and describes the organization of the text.
- A body with paragraphs highlighting central ideas and providing supporting information for them (subtitles can make the structure clearer).
- A conclusion that, rather than condensing the main points, provides lessons learned, possible implications or recommendations to keep in mind.
-
BS03: We must build blog posts with a LIX value below 50 to make them easy to read. (To achieve this, we can use short sentences and short words.)
Images
-
BI01: We must include a cover image taken only from Unsplash for each blog post (it must have a size of 900 × 600 px and less than 800 KB).
-
BI02: We must name the cover image as follows: cover_[main keyword of the post] (e.g., cover_pentesting; both words in lower case).
-
BI03: We can use images from different websites and other sources within the bodies of the blog posts.
-
BI04: We must name each image with a corresponding keyword in lower case. (We can repeat the name with an initial capital letter between the brackets after the link of the image and even accompany it with other keywords.) Example:
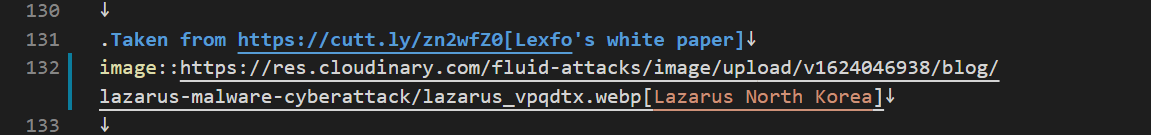
-
BI05: We should put a brief description under each image we use (it must be no longer than 80 characters).
-
BI06: We must include the reference as a hyperlink in the description of each image that does not belong to us. Example:
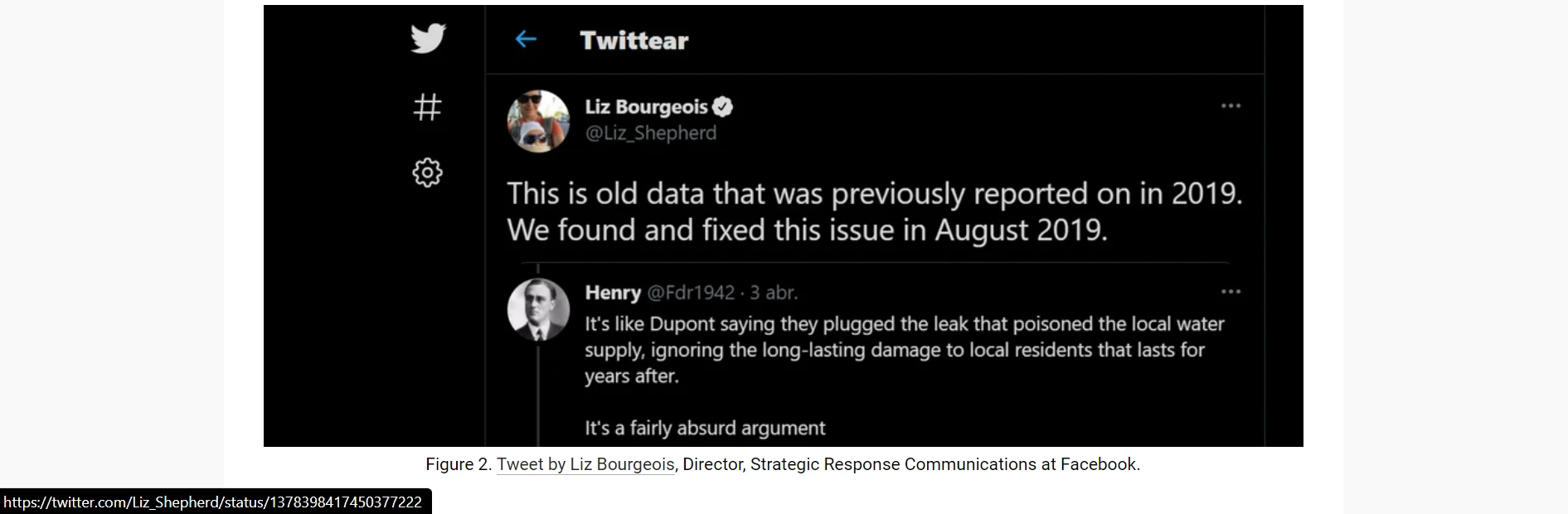
-
BI07: We must always upload the images to Cloudinary and then use their links, changing their filename extensions to .webp inside the .adoc files. (Only for
Fluid Attacksstaff.)
Others
-
BO01: Whenever we create a post with an interview, we must use the
[role="fluid-question"]and[role="fluid-answer"]commands to display each question and answer (this one indented by two spaces) in a specific way. Example: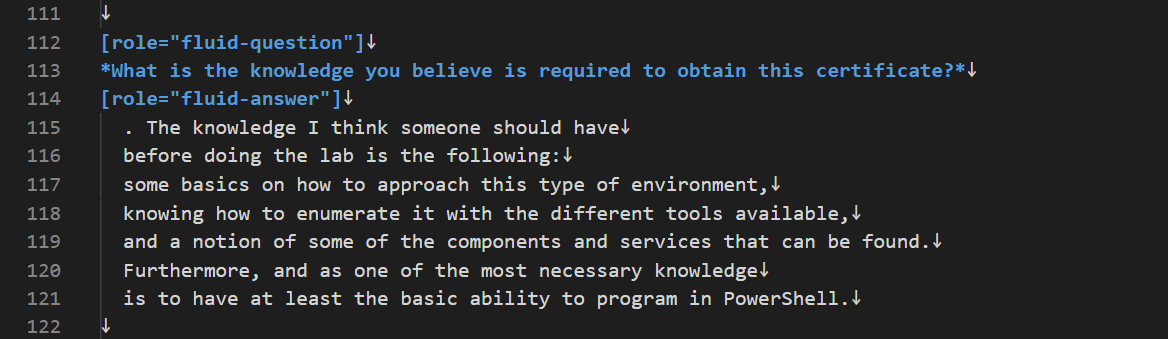
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.