Adding secrets with GCP
Here you can find all the information required by a customer to enroll an GCP cloud account to start using the CSPM DAST module.
You will need two credentials to use the GCP CSPM DAST module.
Manual configuration from GCP cloud console
We'll outline the general steps to create a private key for a Google Cloud service account with the role of Security Reviewer:
GCP Project ID
To obtain the Project ID for a Google Cloud Platform (GCP) account, you can follow these steps
-
Google Cloud Console Login: Log in to your Google Cloud account using the Google Cloud Console at https://console.cloud.google.com/
-
Select a Project: If you are working within a specific project, select that project from the dropdown menu at the top of the Google Cloud Console. The Project ID is associated with a specific project, so make sure you are working within the correct project context.
-
View the Project ID: Once you have selected the correct project (or if you are already in the correct project), you can find the Project ID in a few different places:
-
Dashboard: The Project ID is typically displayed on the Google Cloud Console dashboard, under the project name.
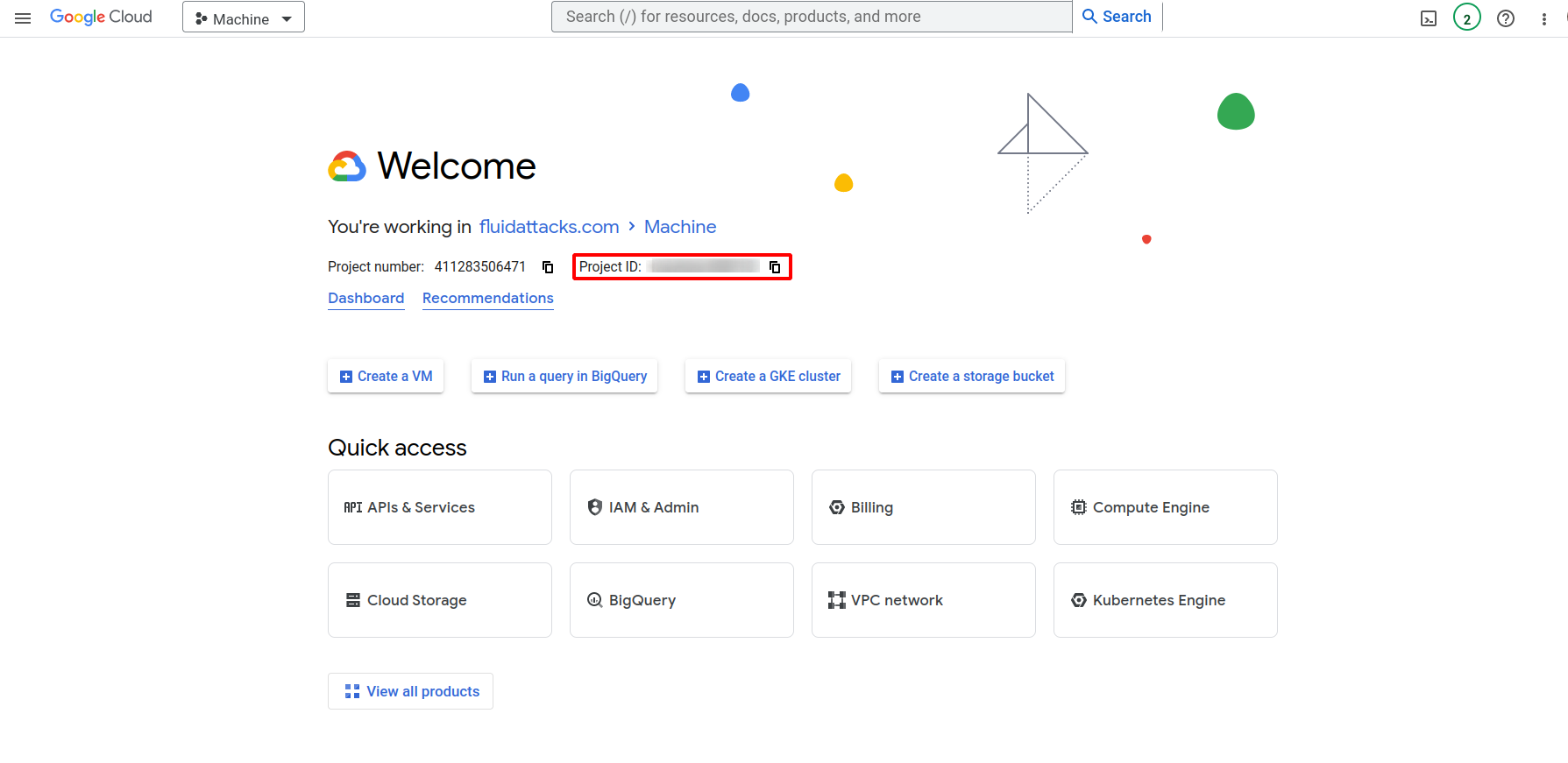
-
Project Settings Page: You can also find the Project ID by clicking on the project name at the top of the Google Cloud Console to open the project selection modal. The Project ID will be displayed there.
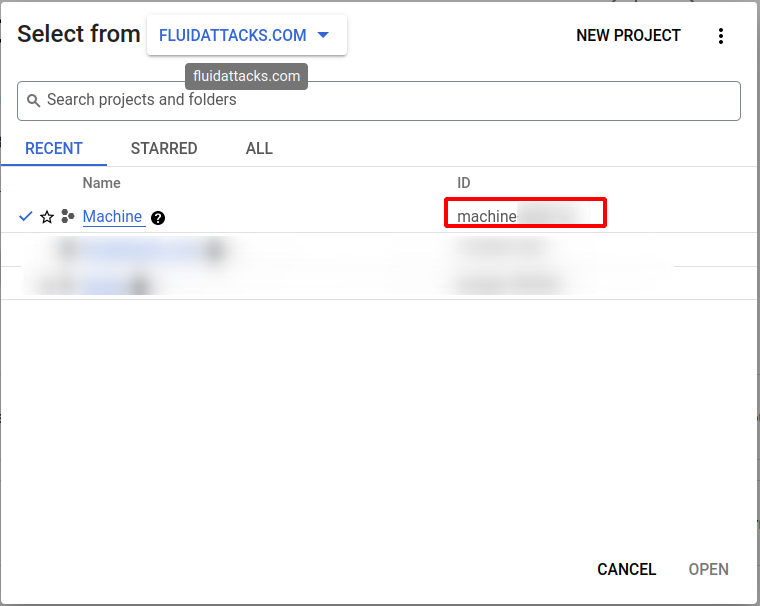
-
GCP service account private key
We'll outline the general steps to create a private key for a Google Cloud service account with the role of Security Reviewer:
-
Access the Google Cloud Console: Log in to your Google Cloud account using the Google Cloud Console.
-
Select Your Project: Ensure you are working within the correct Google Cloud project where you want to create the service account.
-
Navigate to the IAM & Admin Dashboard: In the Google Cloud Console, navigate to the "IAM & Admin" dashboard.
-
Create a Service Account: To create a new service account, click on the "Service accounts" tab within the IAM & Admin dashboard and then click the "Create Service Account" button.
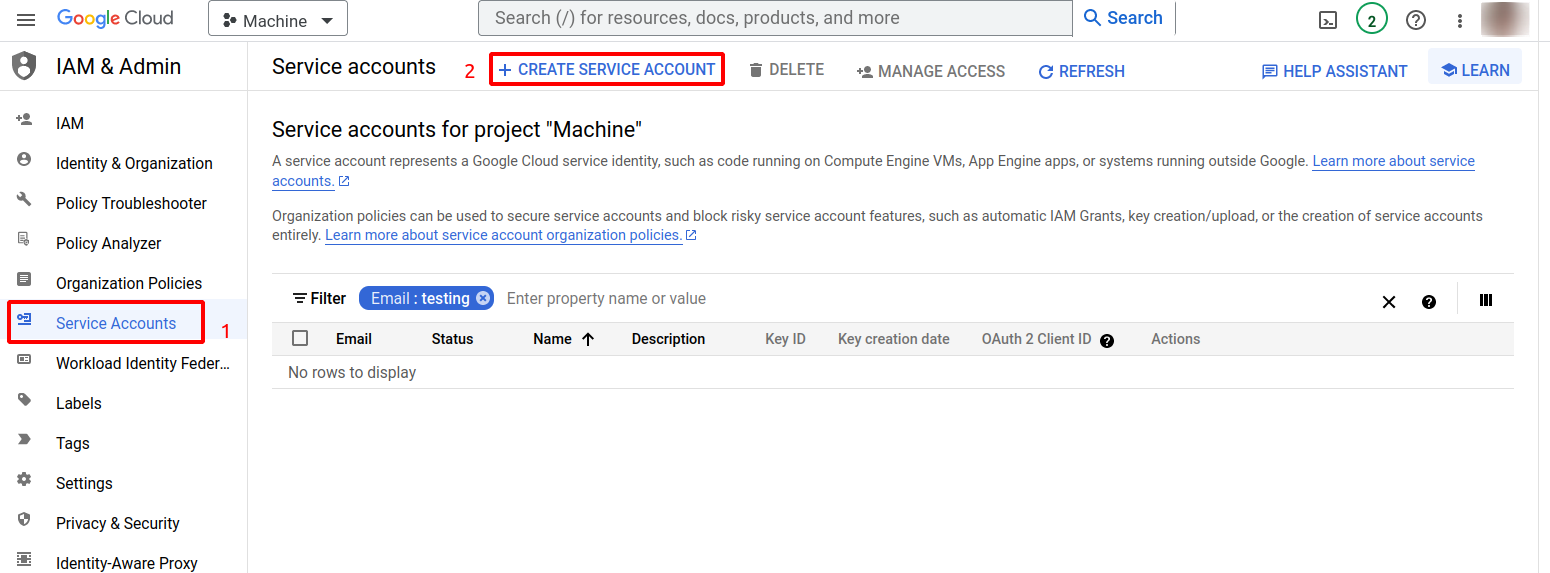
-
Provide a Name and Description: Give your service account a name and optional description that helps you identify its purpose, such as "SecurityReviewerServiceAccount" the click on create and continue
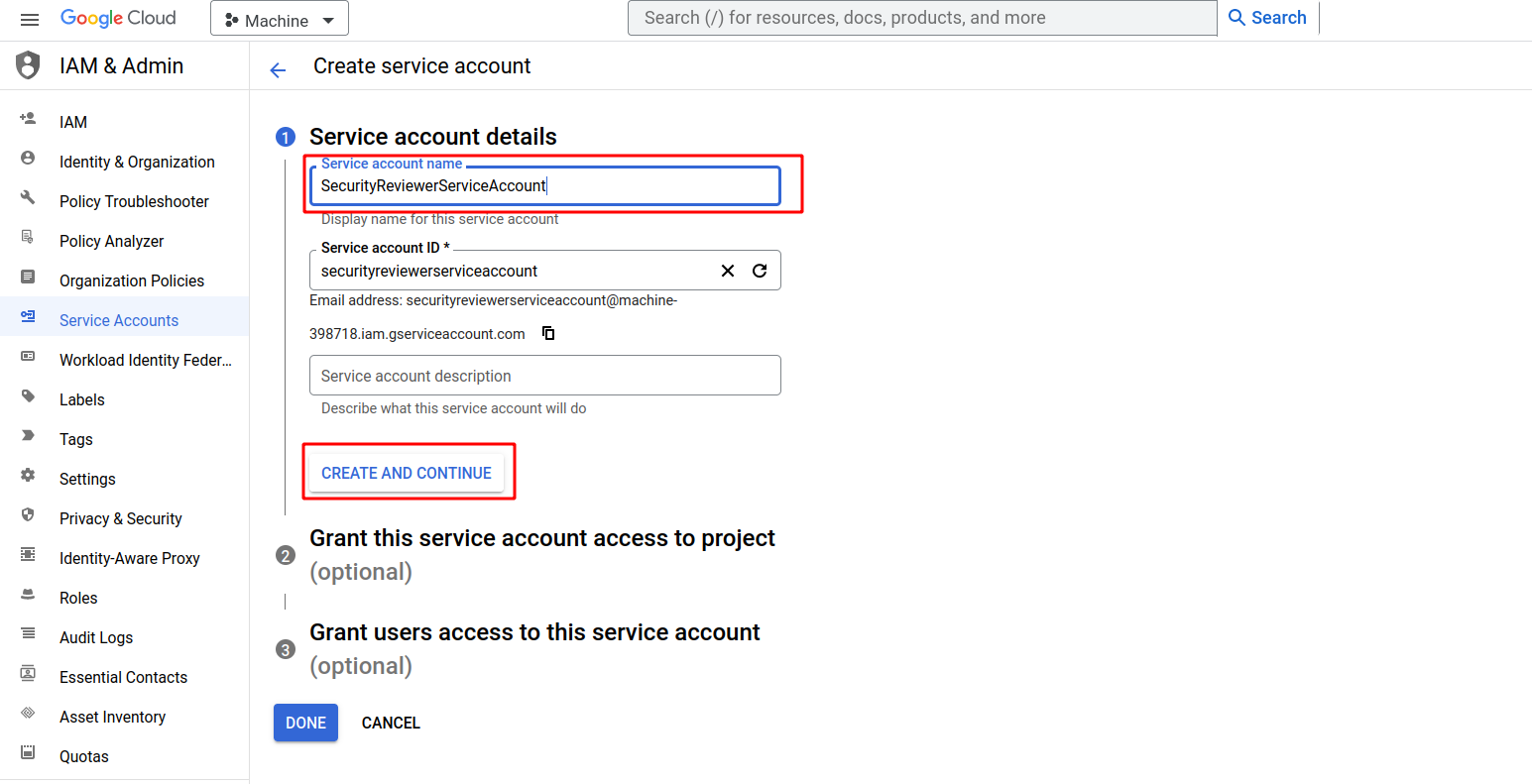
-
Assign the Role of Security Reviewer: In the "Select a role" section, search for and select the "Security Reviewer" role then click continue This role should have permissions to list all resources and allow policies on them.
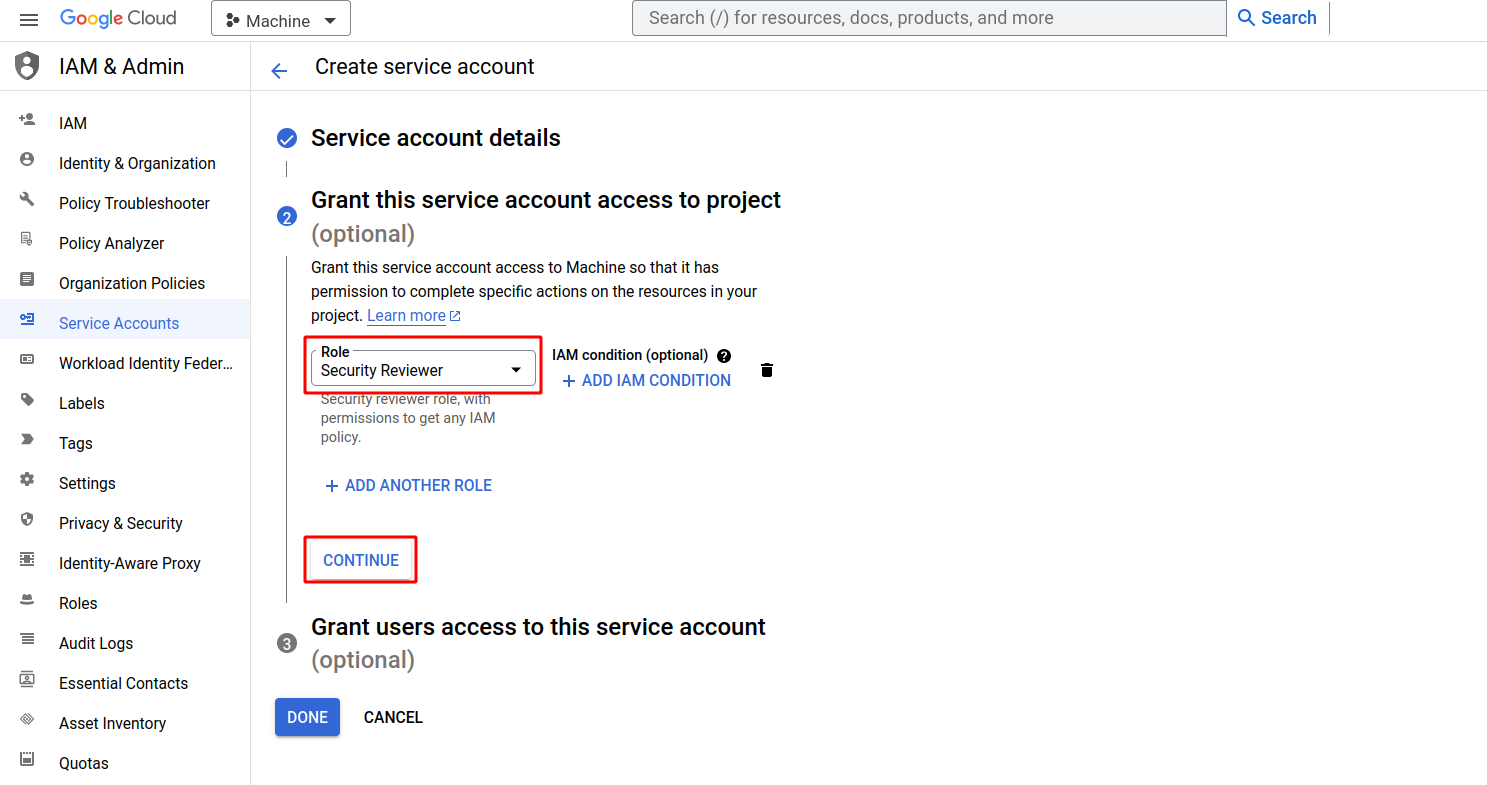
-
Create the Service Account: Click the "Done" button to proceed with creating the service account.
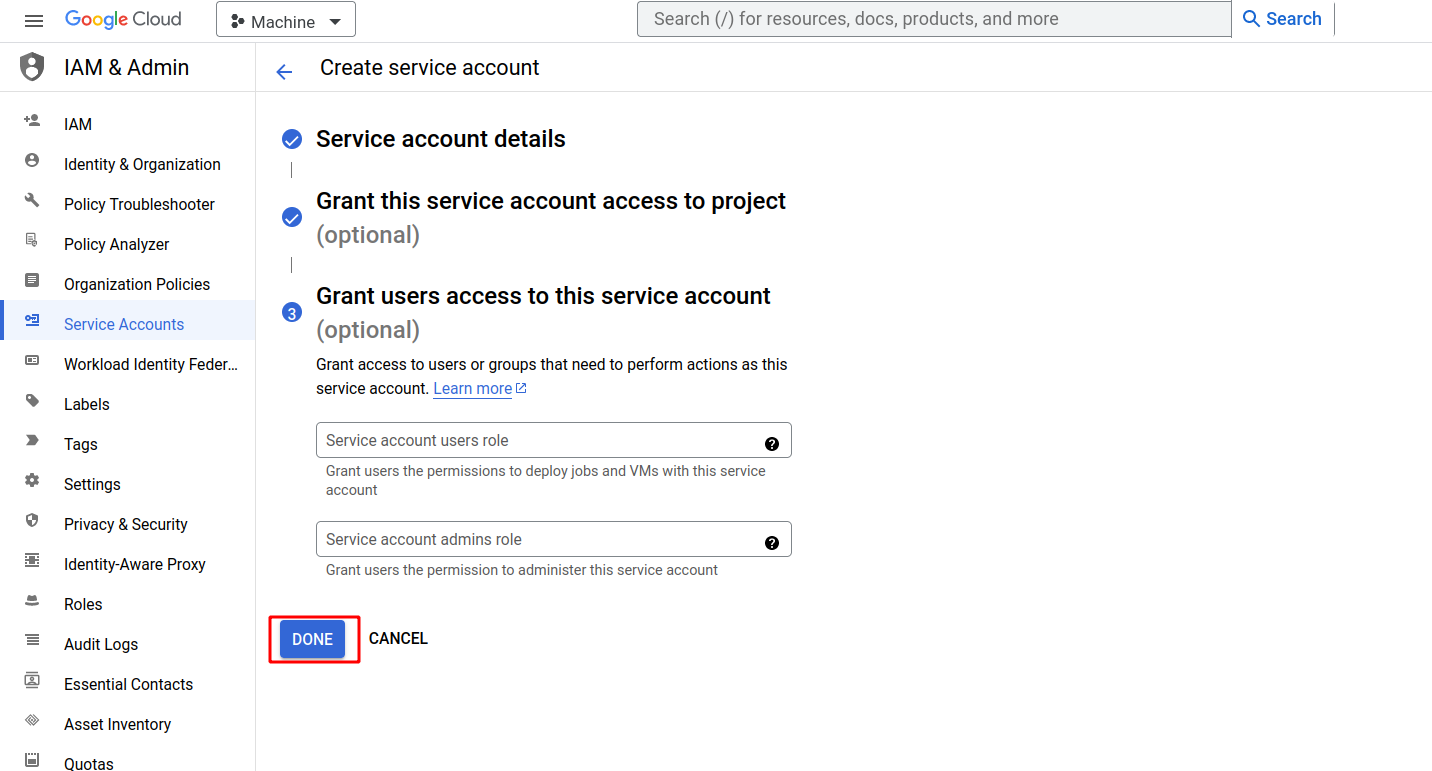
-
Create a Key Pair (Private Key): After creating the service account, you'll get a new security account in the table, click the "Action" button and then click the "Manage Keys" option
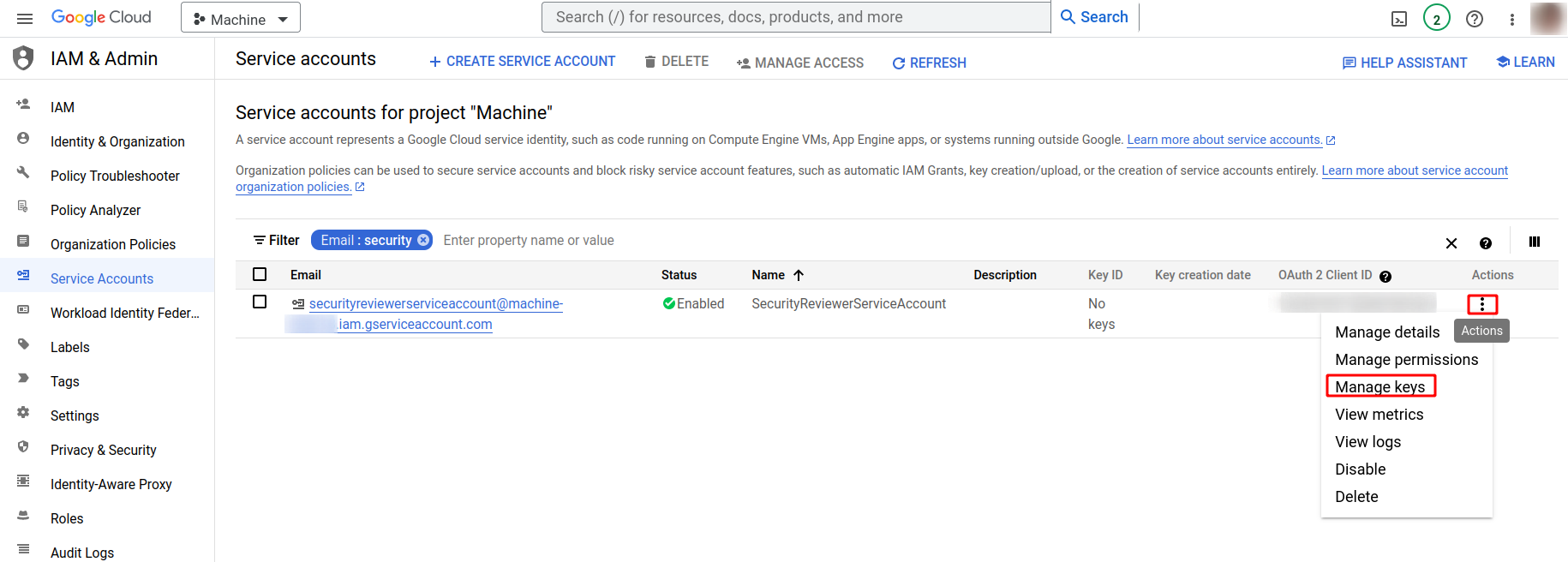
Now in the Manage Keys dashboard click on the ADD KEY button and select Create new key.
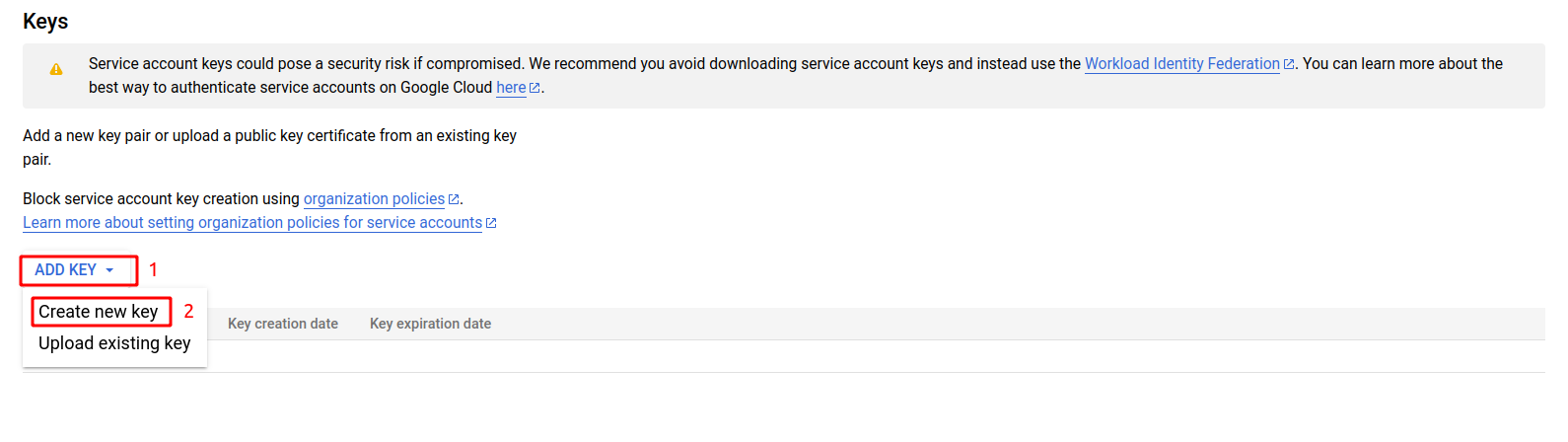
You'll be prompted to create a key pair (private key) for it. Choose the key type, for this case JSON, and click "Create." This will generate and download a JSON key file containing the private key. The content on this file will be the private key to run Fluid Attacks' tool.

-
Store the Key Securely: Keep the JSON key file secure, as it provides access to your service account. Do not expose it publicly or commit it to version control repositories.
GCP setup on Fluid Attacks' platform
If you selected the option to add Google Cloud Platform (GCP) secrets, you must fill in the following fields: GCP project ID and GCP_PRIVATE_KEY. To obtain these values you can check the section GCP Enrollment.
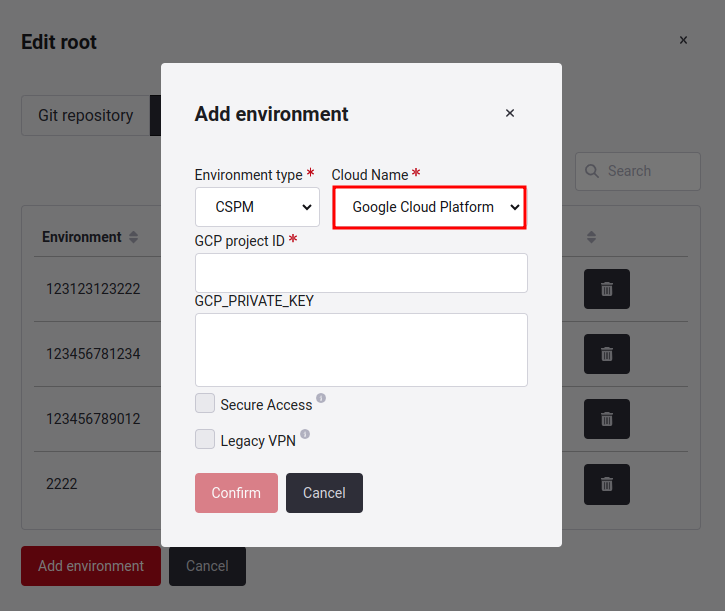
- GCP project ID: The ID that represents that GCP environment; note that it is composed of alphanumeric fields.
- GCP_PRIVATE_KEY: Represents the session key for a service account comprising alphanumeric characters.