Identity and Access Management
Public Oath
Fluid Attacks will look for an Identity and Access Management (IAM) architecture that properly balances security and user comfort.
We will constantly look for better ways of centralizing credentials and access to all of our stack.
Architecture
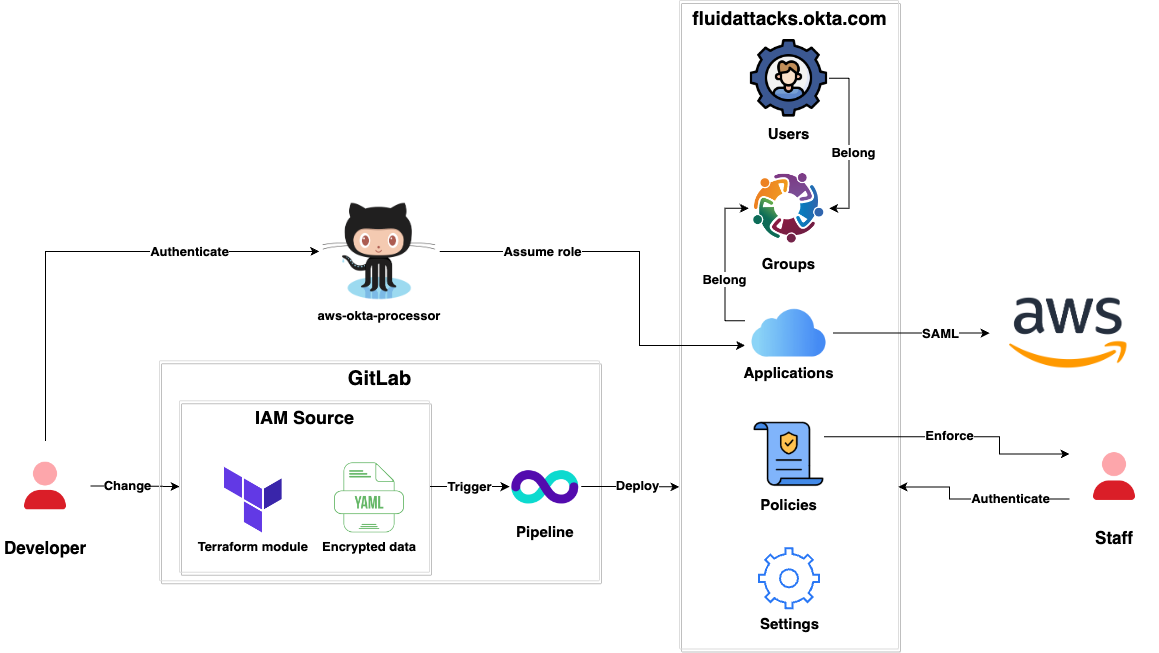
- We use Okta as our main IAM provider.
- It is accessible via fluidattacks.okta.com
- It is managed as code using Terraform.
Below is a comprehensive list:
- Applications
- Groups
- Users
- SAML integration with AWS
- Organization settings
- Passphrases and MFA policies
- Applications, groups and users are stored in encrypted YAML files using Mozilla SOPS as they contain sensitive data like application passphrases and staff personal information.
- Applications are third party solutions used by Fluid Attacks.
- Groups are Fluid Attacks' departments.
- Users are Fluid Attacks' staff.
- Users and applications belong to groups. Meaning that when a user belongs to a group, she can access all applications that belong to that same group.
- Policies are enforced for all staff.
- Developers can assume AWS roles by authenticating to Okta via aws-okta-processor.
Contributing
Please read the contributing page first.