Exclude findings from scan reports
Fluid Attacks offers the NOFLUID feature to allow you to exclude from reports some specific, potentially insecure lines within your application’s source code or infrastructure-as-code (IaC) configurations. This way you can avoid findings that might not be relevant to your specific context.
The procedure to follow depends on the type of vulnerability you want to exclude. In this page you find a description of the different ways to declare an exclusion, along with the cases in which each one is used.
While NOFLUID offers valuable control over scan results, it is crucial to use it responsibly. Excluding findings can mask potential vulnerabilities in your code or misconfigurations. Always ensure you fully understand the implications of excluding a finding and only do so when you have a clear justification. Using this feature means you acknowledge and accept the associated risks.
Exclude with comments
To suppress a specific finding within your code, add the NOFLUID comment to the line before the one flagged by the scanner. Include a brief explanation of why you are excluding this issue.
import * as CryptoJS from "crypto-js";function hasCryptoJsFunctions(arg) { // NOFLUID This report is irrelevant, controlled variable. const Utf16LE = CryptoJS.enc.Utf16LE.parse("a23ijl");}You could also use NOFLUID in dependency declaration files that accept comments in their format:
buildscript { ext { lombokVersion = '1.18.16' } }dependencies { // NOFLUID Assumed risk. compile "io.springfox:springfox-swagger-ui:2.6.0"}Or use it in your IaC configuration file:
resource "test_cluster" "main" { cluster_identifier = "test" database_name = "test" master_username = var.clusterUser master_password = var.clusterPass cluster_type = "single-node" # NOFLUID The cluster is adequately hardened publicly_accessible = true ...}After adding the NOFLUID comment, rerun the static analysis. The scanner now skips the potential security issue.
Exclude with configuration file
For software composition analysis (SCA) scans (which evaluate files where comments are not allowed, such as a package-lock.json ) and dynamic application security testing (DAST) scans (for URL environments), you can define a fluidattacks.yaml file at the root of your project. This file allows you to specify exclusions for specific dependencies or endpoints.
The file format is as follows:
SCA:Note that finding_code is the corresponding location of the vulnerability you want to exclude. You can obtain this from the output of your previous scan.
You can add as many dependencies, URLs and vulnerabilities to exclude as you want.
Example:
SCA:In this example, vulnerabilities for the boto3 and sqllite dependencies are excluded. Additionally, the types of vulnerabilities f043 and f086 for the myapp.com endpoint and type f313 for the web.example.com endpoint are excluded.
Exclude with tag in your AWS resources
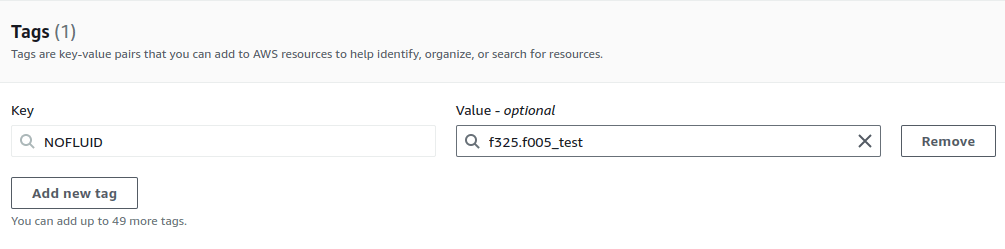
To exclude a finding on your AWS resources, add a tag to the resource with the potential vulnerability. The tag’s key must be NOFLUID, and the value should include the reason for the exclusion and the code of the weakness in the following format:
<finding_code>.<finding_code>..._<reason>The following screenshot shows an example.
To read exclusion tags from your resources, ensure the IAM role assumed by the Fluid Attacks scanner has the following permissions:
- iam:ListUsers
- iam:ListUserTags
- iam:ListRoles
- iam:ListRoleTags
- tag:GetResources
See instructions in Set up an AWS integration .
You can define exclusion tags directly in your IaC templates (e.g., Terraform, CloudFormation). This is particularly useful for resources with short lifespans, as it automates the tagging process.
Here is an example:
resource "aws_instance" "example" { ami = "ami-123456" instance_type = "t2.micro" tags = { Name = "test" NOFLUID = "f001.f002_non_relevant" }}Note: Currently, this feature is not supported for resources that do not allow tags.
Free trial Search for vulnerabilities in your apps for free with Fluid Attacks’ automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan . If you prefer the Advanced plan, which includes the expertise of Fluid Attacks’ hacking team, fill out this contact form .