Fix code automatically with gen AI
Always review the accuracy of remediation suggestions generated with AI.
Fluid Attacks’ Autofix feature allows you to efficiently remediate vulnerabilities within your source code. Leveraging the power of generative AI, Autofix suggests custom modifications that transform your vulnerable code into secure code. Currently, this feature is available for Fluid Attacks’ extensions for VS Code and Cursor .
Below is a simple explanation of how Autofix works and how to use it.
How Autofix works
Autofix sits on Fluid Attacks’ VS Code and Cursor extensions, which retrieve vulnerability reports from Fluid Attacks’ platform to show which lines of code are vulnerable directly in the IDE.
Autofix’s efficiency stems from its integration with Claude 3.5 Sonnet’s advanced code analysis and generation capabilities. This powerful AI model can accurately identify vulnerabilities and produce targeted fixes, saving you time and effort in the remediation process.
Once Autofix receives the code fragment, the model generates specific actions to address and remediate the vulnerability, returning the code with the implemented solution. For details on Fluid Attacks’ usage of Claude to generate fixes and data privacy in relation to it, refer to the IDE extension FAQ .
Use Autofix
The Autofix functionality leverages Claude’s ability to fix vulnerable code automatically. As a prerequisite, you must have installed Fluid Attacks’ VS Code extension or Cursor extension . With the extension installed, follow these steps:
-
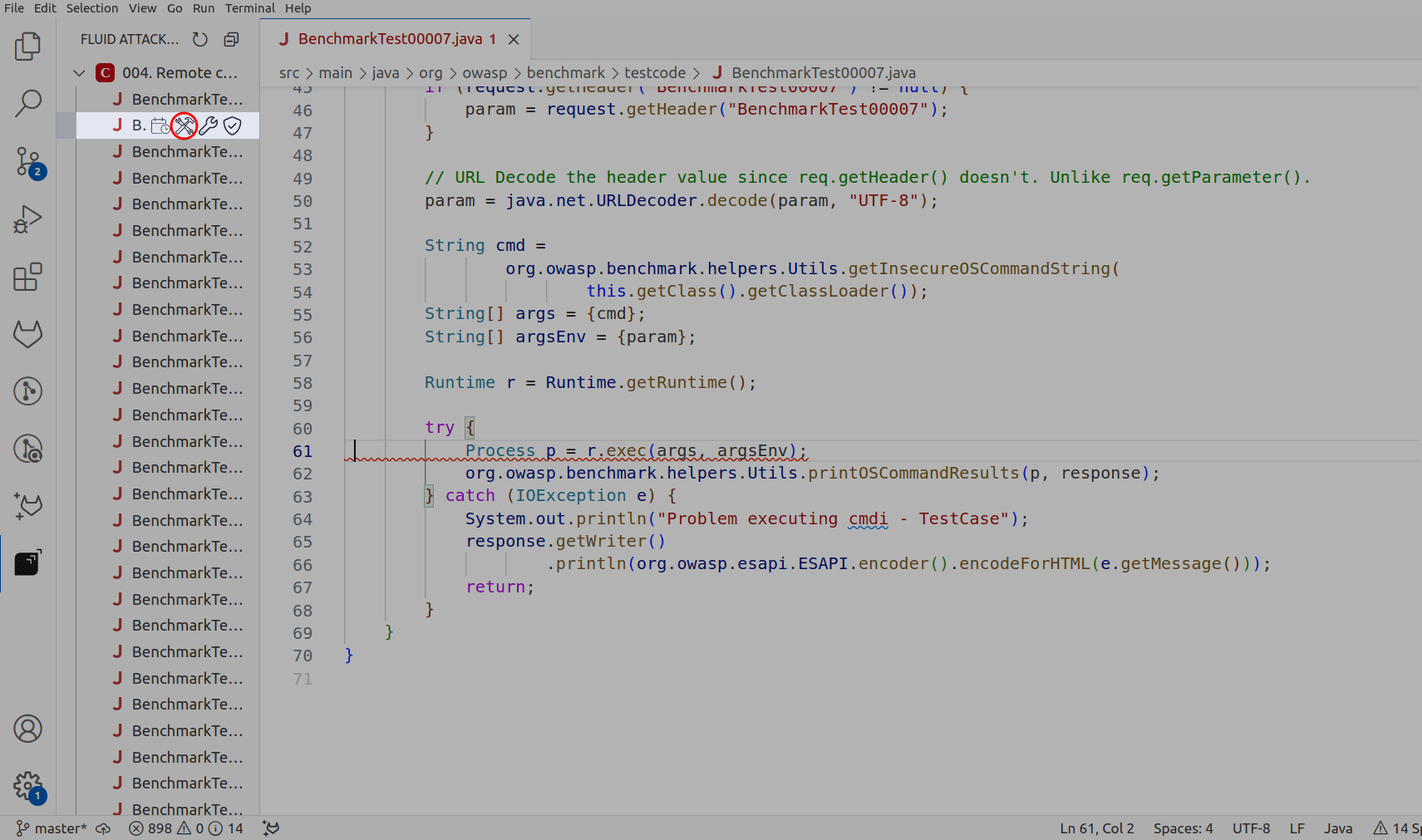
Click on the Fluid Attacks extension in the IDE’s activity bar and locate the file containing the vulnerability you wish to fix.
-
Click the hammer and wrench icon associated with that file to initiate Autofix.
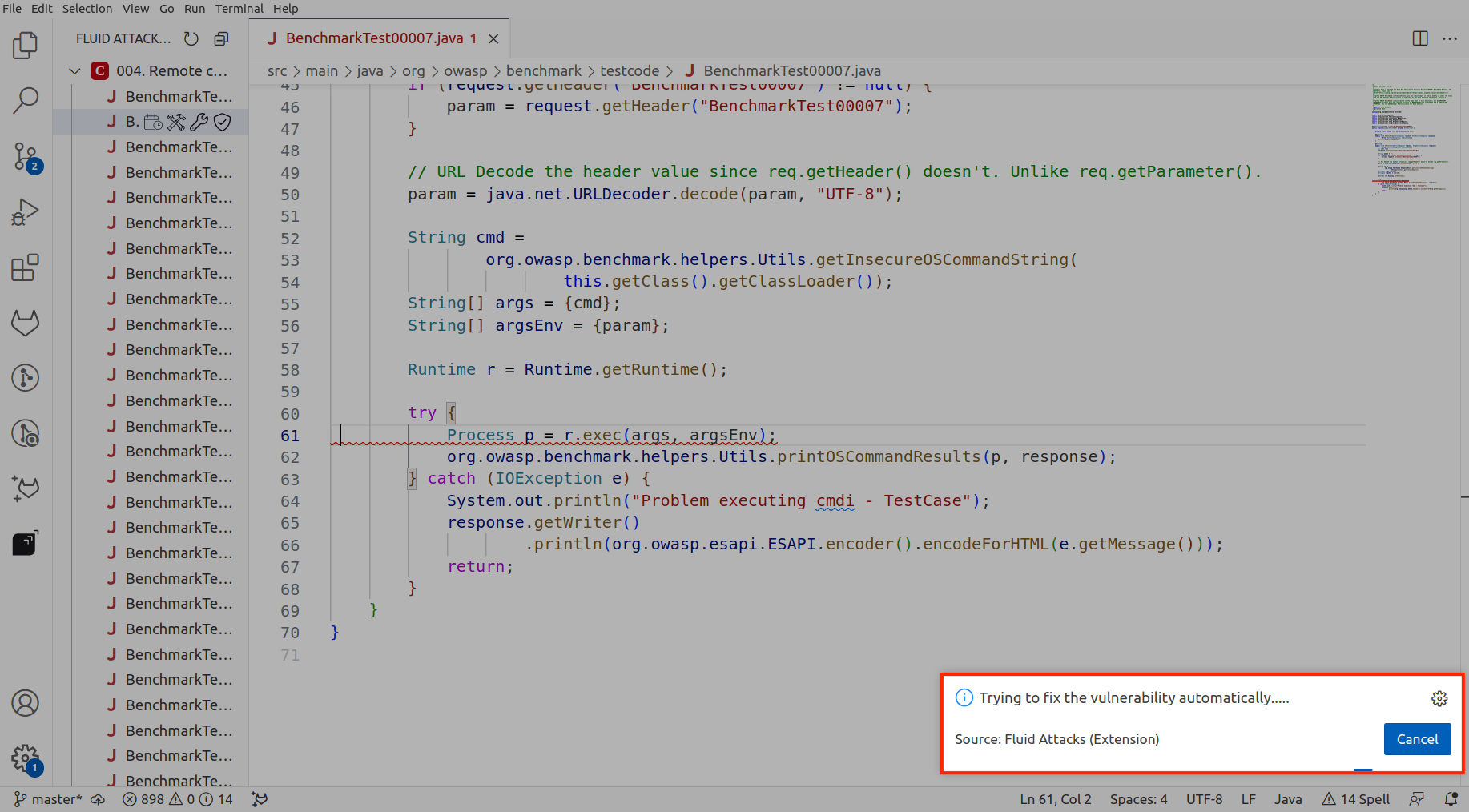
Autofix automatically establishes a connection with Claude’s AI model. This connection enables the model to analyze the code and generate the necessary fixes. During this process, you see the message “Trying to fix the vulnerability automatically.”
-
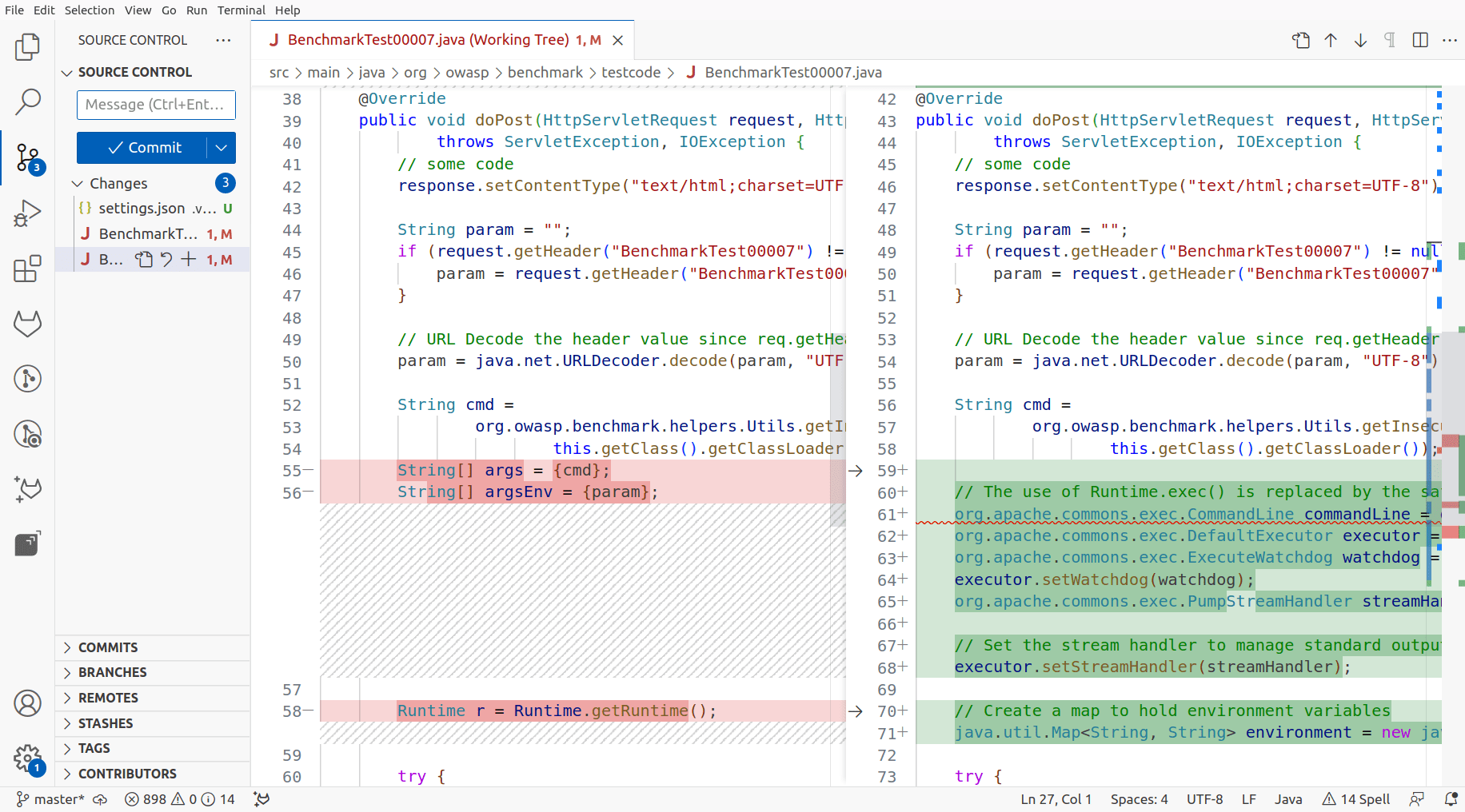
After a few seconds, the code is automatically modified. Review the AI-generated fix suggestion and proceed only after verification that the resulting code is secure.
Fluid Attacks’ GenAI is fed by the Fixes documentation , which supports languages, infrastructure as code (IaC), and configuration files such Android , Azure , CloudFormation , Docker , Docker Compose , Helm , JavaScript , Kotlin , and Terraform.
Search for vulnerabilities in your apps for free with Fluid Attacks’ automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan . If you prefer the Advanced plan, which includes the expertise of Fluid Attacks’ hacking team, fill out this contact form .